Welcome to Day 12 of 21 Days of AWS using Terraform. Topic for today is Introduction to CloudTrail using Terraform
What Is AWS CloudTrail?
AWS CloudTrail is an AWS service that helps you enable governance, compliance, and operational and risk auditing of your AWS account. Actions taken by a user, role, or an AWS service are recorded as events in CloudTrail. Events include actions taken in the AWS Management Console, AWS Command Line Interface, and AWS SDKs and APIs.
- It’s enabled when the account is created(for 7 days)
- When activity occurs in your AWS account, that activity is recorded in a CloudTrail event.
- Entries can be viewed in Event History(for 90 days)
- Event logs can be aggregated across accounts and regions.
NOTE
- Historically CloudTrail was not enabled by default
- It won’t logs events like SSH/RDP only API call.
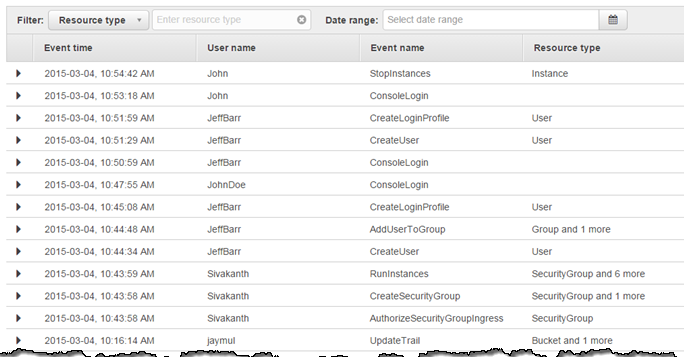
Reference: https://aws.amazon.com/blogs/aws/new-aws-api-activity-lookup-in-cloudtrail/
For an ongoing record of activity and events in your AWS account, create a trail. It allows us to send logs to S3 bucket and can be single or multi-region.
To create a trail
Go to AWS Console --> Management & Governance --> CloudTrail --> Trails --> Create trail
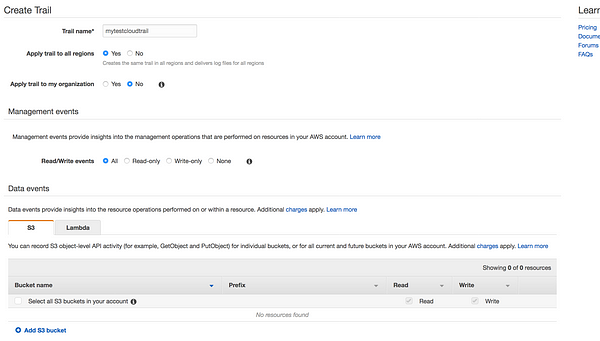
* Trail name: Give your trail name
* Apply trail to all regions: You have an option to choose all regions or specific region.
* Read/Write events: You have the option to filter the events
* Data events: Data events provide insights into the resource operations performed on or within a resource
S3: You can record S3 object-level API activity (for example, GetObject and PutObject) for individual buckets, or for all current and future buckets in your AWS account
Lambda:You can record Invoke API operations for individual functions, or for all current and future functions in your AWS account.
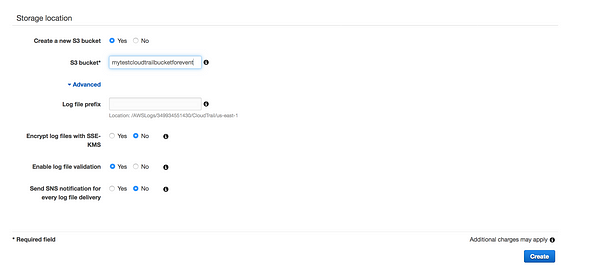
* Storage Locations: Where to store the logs, we can create new bucket or use existing bucket
* Log file prefix: We have the option to provide prefix, this will make it easier to browse log file
* Encrypt log file with SSE-KMS:Default SSE-S3 Server side encryption(AES-256) or we can use KMS
* Enable log file validation: To determine whether a log file was modified, deleted, or unchanged after CloudTrail delivered it, you can use CloudTrail log file integrity validation
* Send SNS notification for every log file delivery:SNS notification of log file delivery allow us to take action immediately
NOTE:
- There is always a delay between when the event occurs vs displayed on CloudTrail dashboard. On top of that, there is an additional delay when that log will be transferred to S3 bucket.
- Delivered every 5(active) minutes with up to 15-minute delay
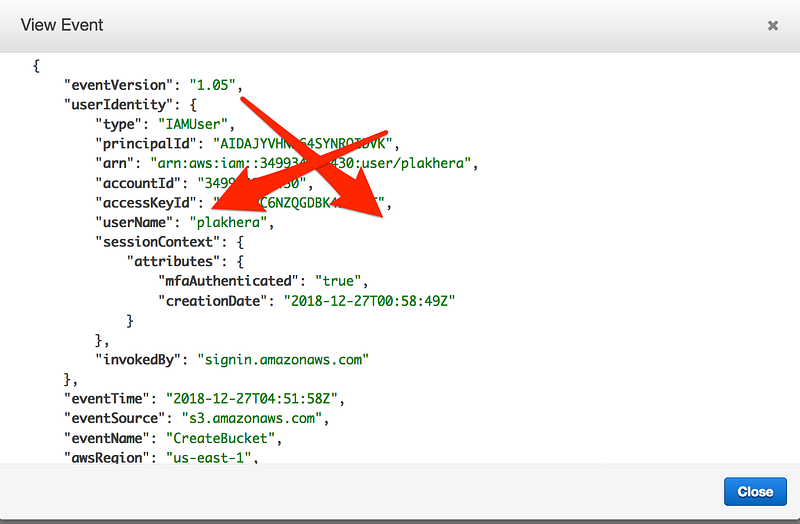
- All CloudEvents are JSON structure you will see something like this when you try to view any event
Terraform Code
resource "aws_cloudtrail" "my-demo-cloudtrail" {
name = "${var.cloudtrail_name}"
s3_bucket_name = "${aws_s3_bucket.s3_bucket_name.id}"
include_global_service_events = true
is_multi_region_trail = true
enable_log_file_validation = true
}name– Specifies the name of the trail.s3_bucket_name– Specifies the name of the S3 bucket designated for publishing log files.include_global_service_events– Specifies whether the trail is publishing events from global services such as IAM to the log files. Defaults totrue.is_multi_region_trail– Specifies whether the trail is created in the current region or in all regions. Defaults tofalse.enable_log_file_validation– Specifies whether log file integrity validation is enabled. Defaults tofalse.
Then we have S3 bucket policy which allows us to send logs to S3 bucket and can be single or multi-region.
resource "aws_s3_bucket" "s3_bucket_name" {
bucket = "${var.s3_bucket_name}"
policy = <<POLICY
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AWSCloudTrailAclCheck",
"Effect": "Allow",
"Principal": {
"Service": "cloudtrail.amazonaws.com"
},
"Action": "s3:GetBucketAcl",
"Resource": "arn:aws:s3:::s3-cloudtrail-bucket-with-terraform-code"
},
{
"Sid": "AWSCloudTrailWrite",
"Effect": "Allow",
"Principal": {
"Service": "cloudtrail.amazonaws.com"
},
"Action": "s3:PutObject",
"Resource": "arn:aws:s3:::s3-cloudtrail-bucket-with-terraform-code/*",
"Condition": {
"StringEquals": {
"s3:x-amz-acl": "bucket-owner-full-control"
}
}
}
]
}
POLICY
}GitHub Link
https://github.com/100daysofdevops/21_days_of_aws_using_terraform/tree/master/cloudtrail
Looking forward for you guys to join this journey
- Website: https://100daysofdevops.com/
- Twitter: @100daysofdevops OR @lakhera2015
- Facebook: https://www.facebook.com/groups/795382630808645/
- Medium: https://medium.com/@devopslearning
- GitHub: https://github.com/100daysofdevops/100daysofdevops
- Slack: https://join.slack.com/t/100daysofdevops/shared_invite/enQtNzg1MjUzMzQzMzgxLWM4Yjk0ZWJiMjY4ZWE3ODBjZjgyYTllZmUxNzFkNTgxZjQ4NDlmZjkzODAwNDczOTYwOTM2MzlhZDNkM2FkMDA
- YouTube Channel: https://www.youtube.com/user/laprashant/videos?view_as=subscriber
In addition to that, I am going to host 5 meetups whose aim is to build the below architecture.

- Meetup: https://www.meetup.com/100daysofdevops
- Day1(Nov 10): Introduction to Terraform https://www.meetup.com/100daysofdevops/events/266192294/
- Day 2(Nov 16): Building VPC using Terraform
- Day 3(Nov 17): Creating EC2 Instance inside this VPC using Terraform
- Day 4(Nov 23): Adding Application Load Balancer and Auto-Scaling to the EC2 instance created on Day 3
- Day5(Nov 24): Add Backend MySQL Database and CloudWatch Alarm using Terraform

Life saver …
Many thanks to you !!!