Welcome to Day 6 of 21 Days of AWS using Terraform. Topic for today is Introduction to Simple Notification to Service(SNS) using terraform.
What is SNS?
As per official documentation
AWS SNS is a web service that coordinates and manages the delivery or sending of messages to subscribing endpoints or clients.
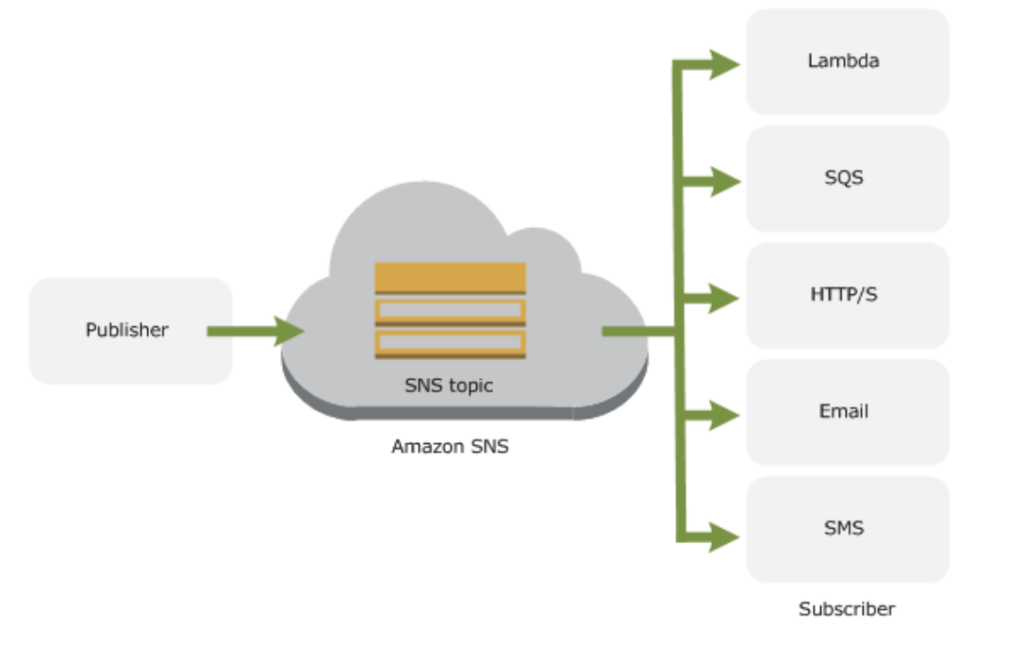
In case of cloudwatch(high CPU utilization or System/Instance Status Check) when the certain event occurs and SNS is used to send a notification. CloudWatch in combination with SNS creates a full monitoring solution with notifies the administrator in case of any environment issue(high CPU, Downtime…).
https://docs.aws.amazon.com/sns/latest/dg/welcome.html
SNS has three major components
Publisher
- The entity that triggers the sending of a message(eg: CloudWatch Alarm, Any application or S3 events)
Topic
- Object to which you publish your message(≤256KB)
- Subscriber subscribe to the topic to receive the message
- Soft limit of 10 million subscribers
Subscriber
An endpoint to a message is sent. Message are simultaneously pushed to the subscriber
- As you can see it follows the publish-subscribe(pub-sub) messaging paradigm with notification being delivered to the client using a push mechanism that eliminates the need to periodically check or poll for new information and updates.
- To prevent the message from being lost, all messages published to Amazon SNS are stored redundantly across multiple Availability Zones.
Enough of theory, let see SNS in action
Using the AWS Console
Step 1: Create a topic
- In the Amazon SNS console, choose Create topic.
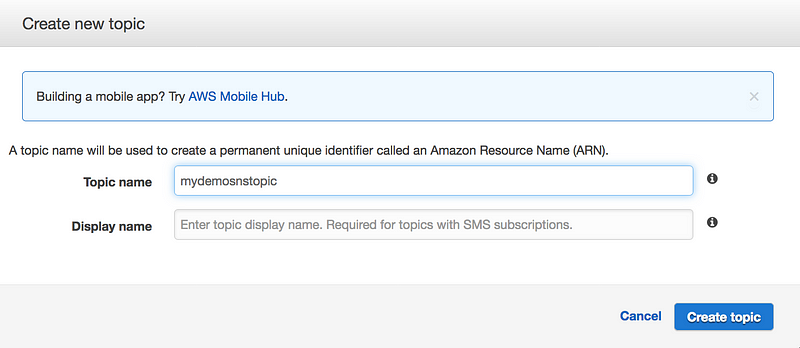
- Create a topic
Step2: Subscribe to a Topic
- Choose to Create a subscription.
- The Create Subscription dialog box appears.
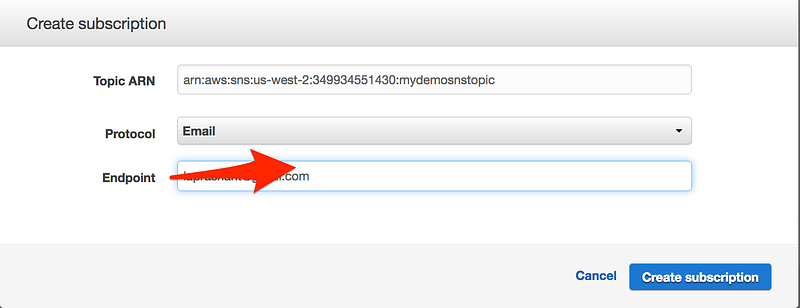
- Go to your email and confirm subscription
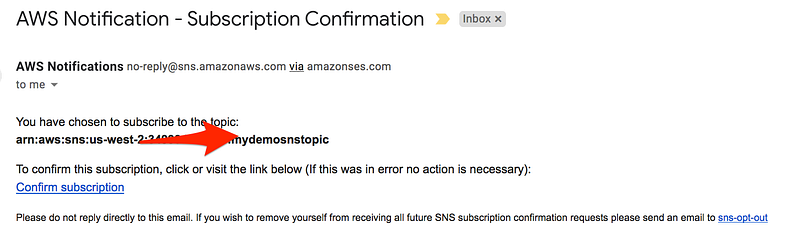
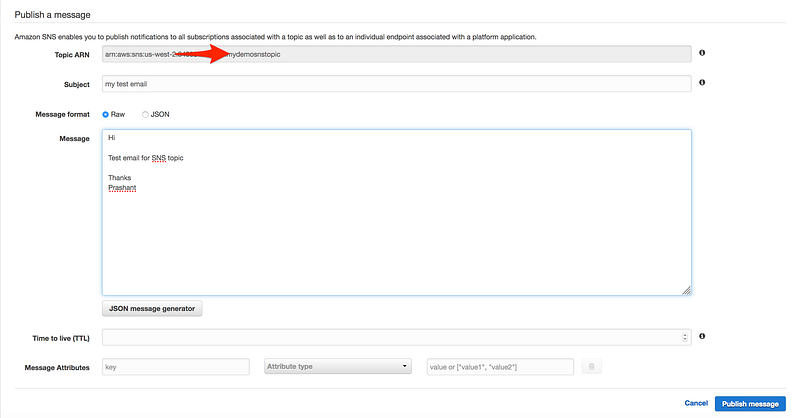
Step3: Publish to the topic
- Choose the Publish to the topic button.
- The Publish a Message page appears.
Let’s check the terraform code
resource "aws_sns_topic" "my-test-alarm" {
name = "my-test-alarms-topic"
delivery_policy = <<EOF
{
"http": {
"defaultHealthyRetryPolicy": {
"minDelayTarget": 20,
"maxDelayTarget": 20,
"numRetries": 3,
"numMaxDelayRetries": 0,
"numNoDelayRetries": 0,
"numMinDelayRetries": 0,
"backoffFunction": "linear"
},
"disableSubscriptionOverrides": false,
"defaultThrottlePolicy": {
"maxReceivesPerSecond": 1
}
}
}
EOF
provisioner "local-exec" {
command = "aws sns subscribe --topic-arn ${self.arn} --protocol email --notification-endpoint ${var.alarms_email}"
}
}name– The friendly name for the SNS topic. By default generated by Terraform.
delivery_policy– The SNS delivery policy. For more info https://docs.aws.amazon.com/sns/latest/dg/sns-message-delivery-retries.html
- The
local-execprovisioner invokes a local executable after a resource is created. This invokes a process on the machine running Terraform, not on the resource. For more info https://www.terraform.io/docs/provisioners/local-exec.html
variables.tf
variable "alarms_email" {}outputs.tf
output "sns_arn" {
value = "${aws_sns_topic.my-test-alarm.arn}"
}Final SNS Module will look like this
module "sns_topic" {
source = "./sns"
alarms_email = "[email protected]"
}GitHub Link
https://github.com/100daysofdevops/21_days_of_aws_using_terraform/tree/master/sns
Looking forward for you guys to join this journey
- Website: https://100daysofdevops.com/
- Twitter: @100daysofdevops OR @lakhera2015
- Facebook: https://www.facebook.com/groups/795382630808645/
- Medium: https://medium.com/@devopslearning
- GitHub: https://github.com/100daysofdevops/100daysofdevops
- Slack: https://join.slack.com/t/100daysofdevops/shared_invite/enQtNzg1MjUzMzQzMzgxLWM4Yjk0ZWJiMjY4ZWE3ODBjZjgyYTllZmUxNzFkNTgxZjQ4NDlmZjkzODAwNDczOTYwOTM2MzlhZDNkM2FkMDA
- YouTube Channel: https://www.youtube.com/user/laprashant/videos?view_as=subscriber
In addition to that, I am going to host 5 meetups whose aim is to build the below architecture.

- Meetup: https://www.meetup.com/100daysofdevops
- Day1(Nov 10): Introduction to Terraform https://www.meetup.com/100daysofdevops/events/266192294/
- Day 2(Nov 16): Building VPC using Terraform
- Day 3(Nov 17): Creating EC2 Instance inside this VPC using Terraform
- Day 4(Nov 23): Adding Application Load Balancer and Auto-Scaling to the EC2 instance created on Day 3
- Day5(Nov 24): Add Backend MySQL Database and CloudWatch Alarm using Terraform
