Welcome to Day 14 of 21 Days of AWS using Terraform. The topic for today is Introduction to Transit Gateway using Terraform
During ReInvent 2018, AWS released a bunch of Products
https://aws.amazon.com/about-aws/whats-new/2018/11/introducing-aws-transit-gateway/
But if you ask me one product which stands out among these is Transit Gateway.
What is Transit Gateway?
AWS Transit Gateway is a service that enables customers to connect their Amazon Virtual Private Clouds (VPCs) and their on-premises networks to a single gateway
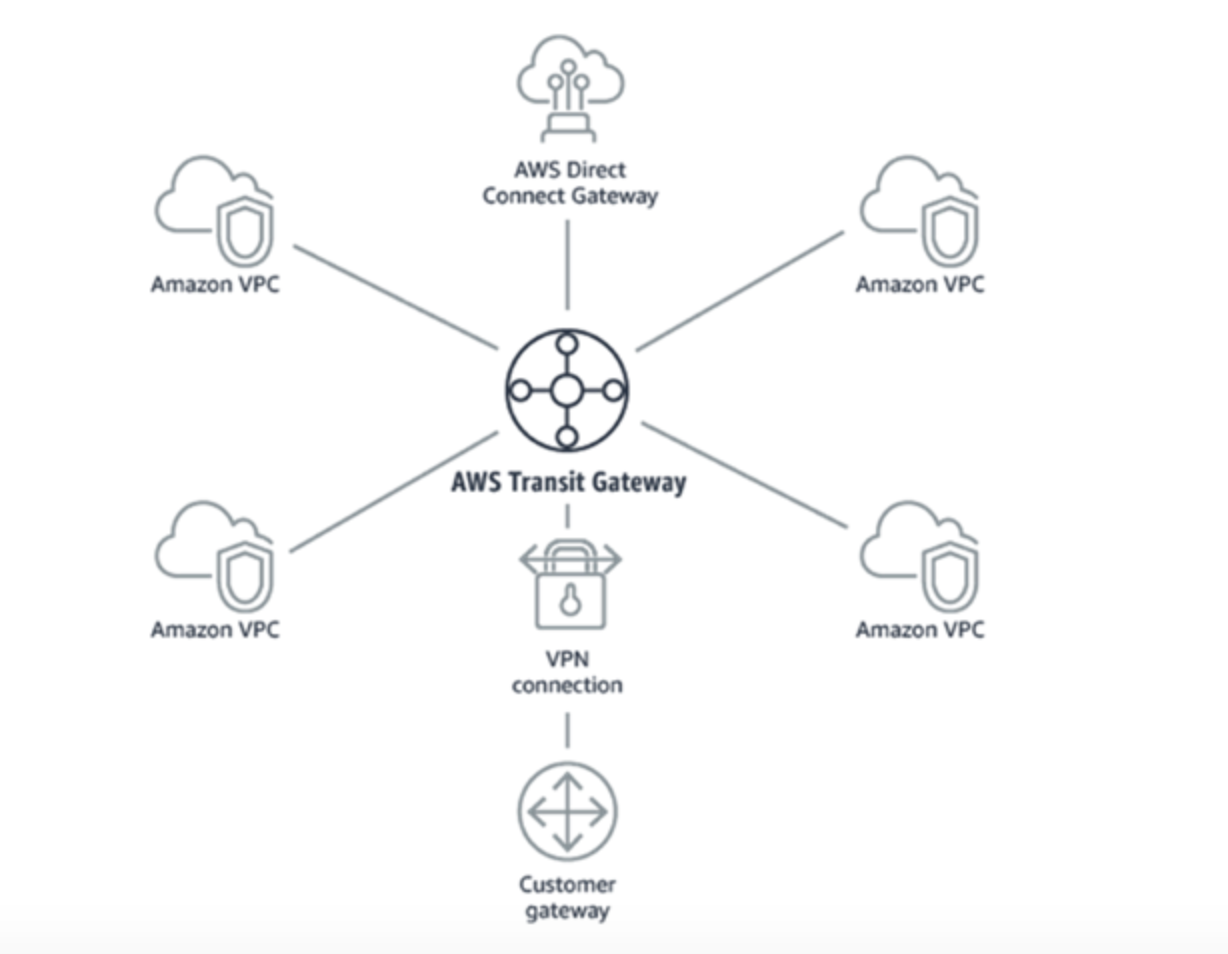
Features of Transit Gateway
- Connect thousands of Amazon Virtual Private Clouds (VPCs) and on-premises networks using a single gateway
- Hub and Spoke Network Topology
- Scales up to 5000 VPCs
- Spread traffic over many VPN connections (Scale horizontally eg: Now two VPN connection combined together give 2.5GBPS(1.25GBPS + 1.25GBPS)
- Max throughput AWS tested so far is 50GBPS
- Direct Connect is still not supported(In AWS 2019 Roadmap)
- Under the hood, to make this happen AWS is using a technology called Hyperplane(https://twitter.com/awsreinvent/status/935740155499040768?lang=en)
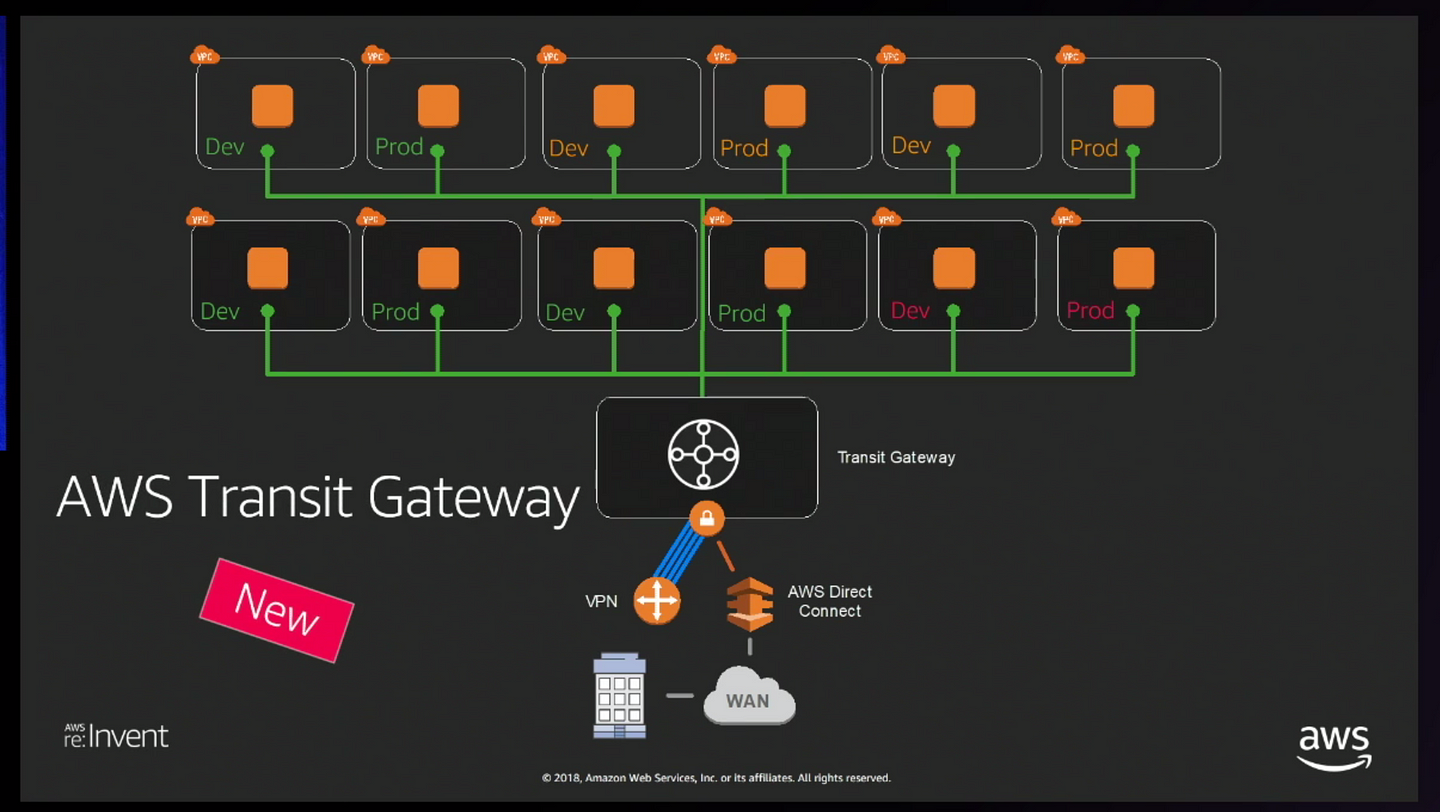
- Transit gateway each route table support 10000 routes(in case of VPC default route table limit is still 100)
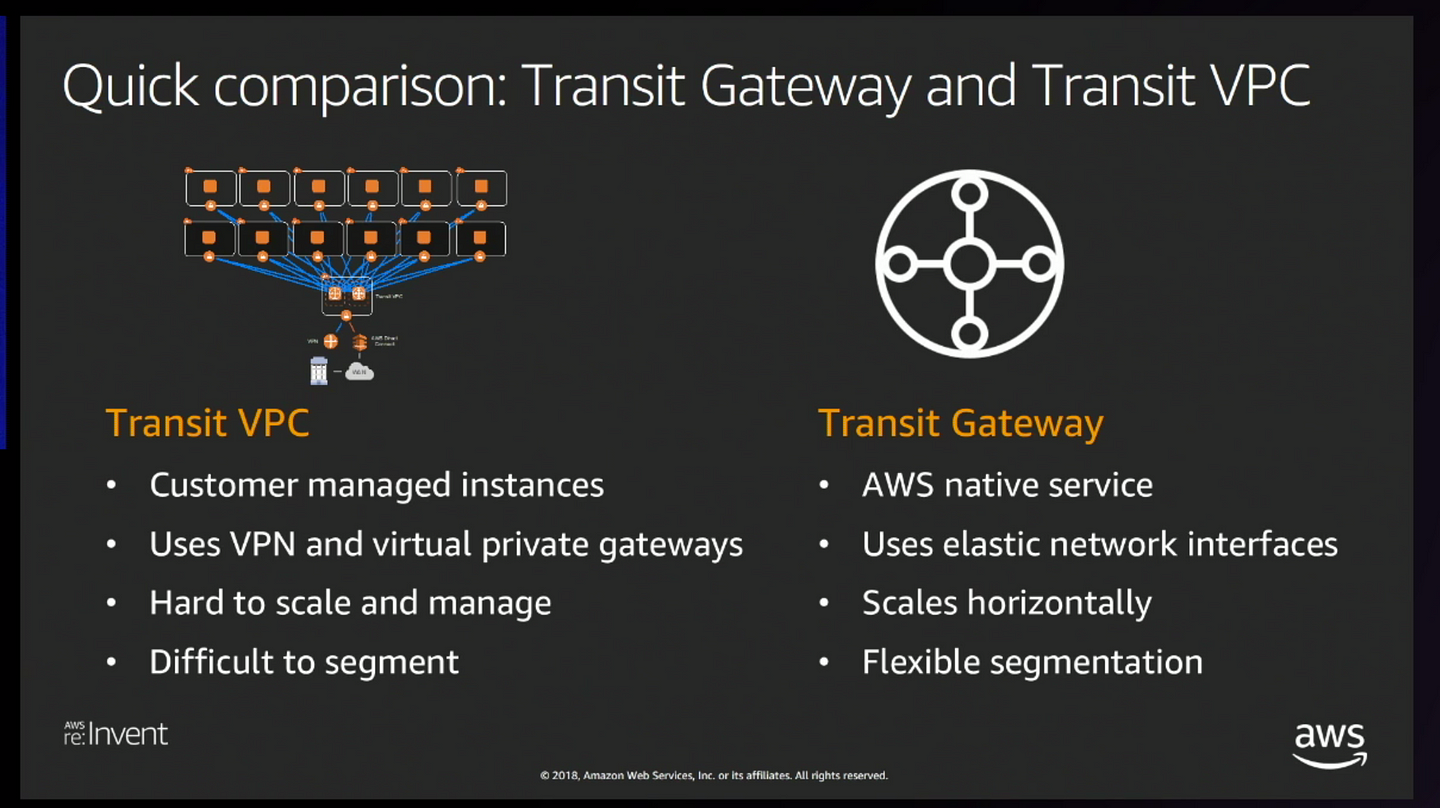
- Difference between Transit VPC vs Transit gateway
- Transit Gateway is available under VPC console
Step1: Build TGW
Go to https://us-west-2.console.aws.amazon.com/vpc → Transit Gateways → Transit Gateways --> Create Transit Gateway
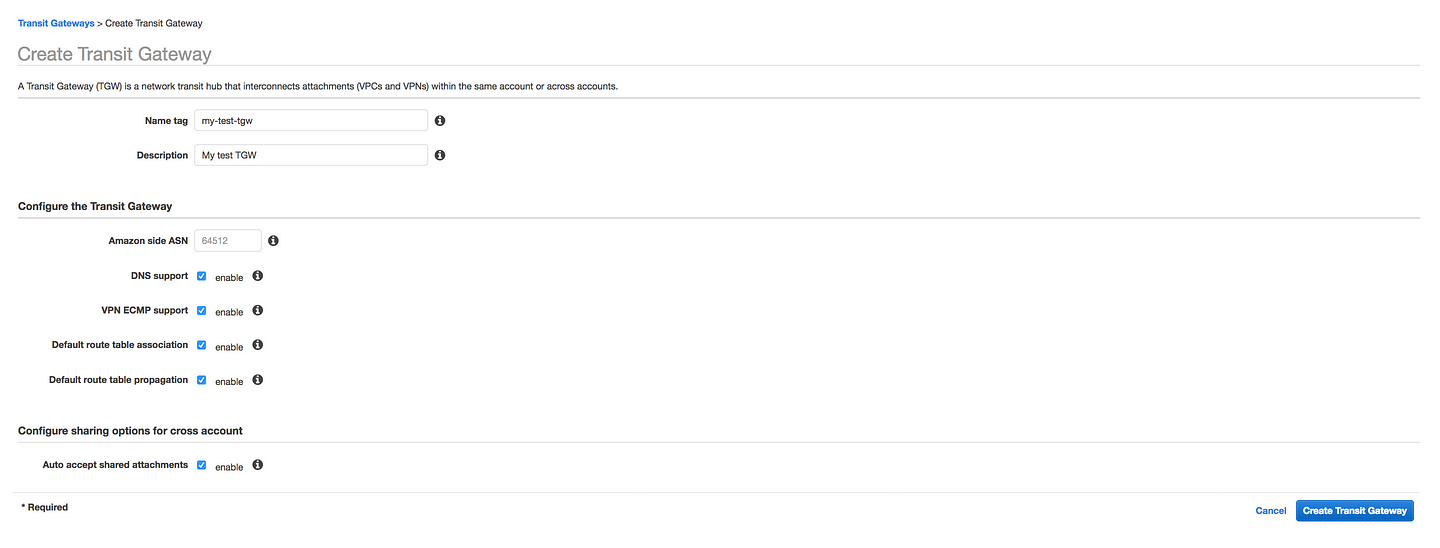
* Name tag and Description: Give some meaningful name to your Transit Gateway and Description
* Amazon side ASN: Autonomous System Number (ASN) of your Transit Gateway. You can use an existing ASN assigned to your network. If you don't have one, you can use a private ASN in the 64512-65534 or 4200000000-4294967294 range.
* DNS Support: Enable Domain Name System resolution for VPCs attached to this Transit Gateway(If you have multiple VPC, this will enable hostname resolution between two VPC)
*VPN ECMP support: Equal-cost multi-path routing for VPN Connections that are attached to this Transit Gateway.Equal Cost Multipath (ECMP) routing support between VPN connections. If connections advertise the same CIDRs, the traffic is distributed equally between them.
* Default route table association: Automatically associate Transit Gateway attachments with this Transit Gateway's default route table.
* Default route table propagation: Automatically propagate Transit Gateway attachments with this Transit Gateway's default route table
* Auto accept shared attachments: Automatically accept cross account attachments that are attached to this Transit Gateway.In case if you are planning to spread your TGW across multiple account.
Terraform Code
resource "aws_ec2_transit_gateway" "my-test-tgw" {
description = "my-test-transit-gateway"
amazon_side_asn = 64512
auto_accept_shared_attachments = "disable"
default_route_table_association = "enable"
default_route_table_propagation = "enable"
dns_support = "enable"
vpn_ecmp_support = "enable"
tags {
Name = "my-test-transit-gateway"
}
}Step2: Attach your VPC
Go to Transit Gateways --> Transit Gateway Attachments --> Create Transit Gateway Attachment
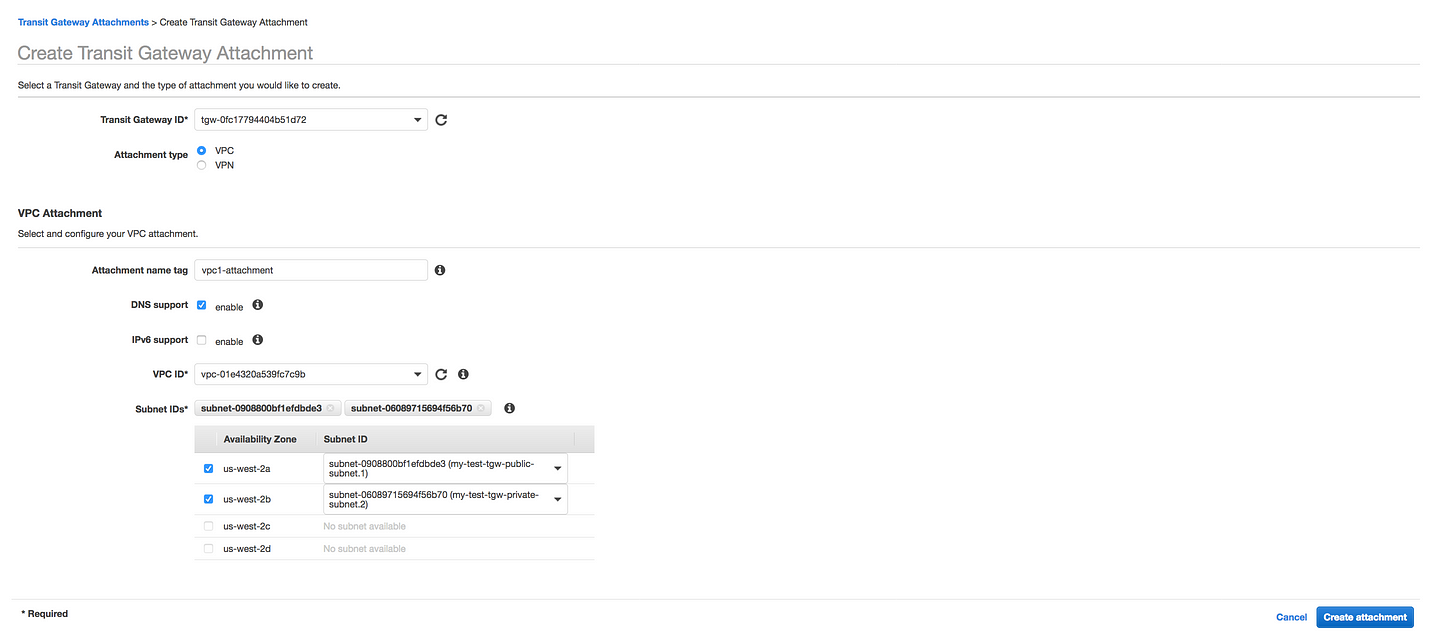
* Select your TGW created in Step1
* Give your VPC attachment some name
* Enable DNS support
* Select your first VPC
- Perform the same step for VPC2
NOTE: When you attach a VPC or create a VPN connection on a transit gateway, the attachment is associated with the default route table of the transit gateway.
resource "aws_ec2_transit_gateway_vpc_attachment" "my-test-transit-gateway-attachment" {
transit_gateway_id = "${aws_ec2_transit_gateway.my-test-tgw.id}"
vpc_id = "${var.vpc_id}"
dns_support = "enable"
subnet_ids = [
"${var.public_subnet1}",
"${var.public_subnet2}",
]
tags {
Name = "my-test-tgw-vpc-attachment"
}
}Step3: Update Route Table
- If you click on the Transit Gateway Route Table, you will see we have the patch from Transit Gateway to our VPC
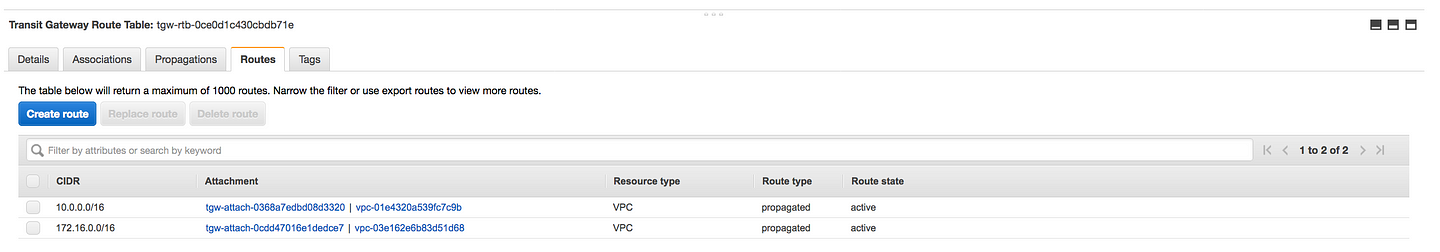
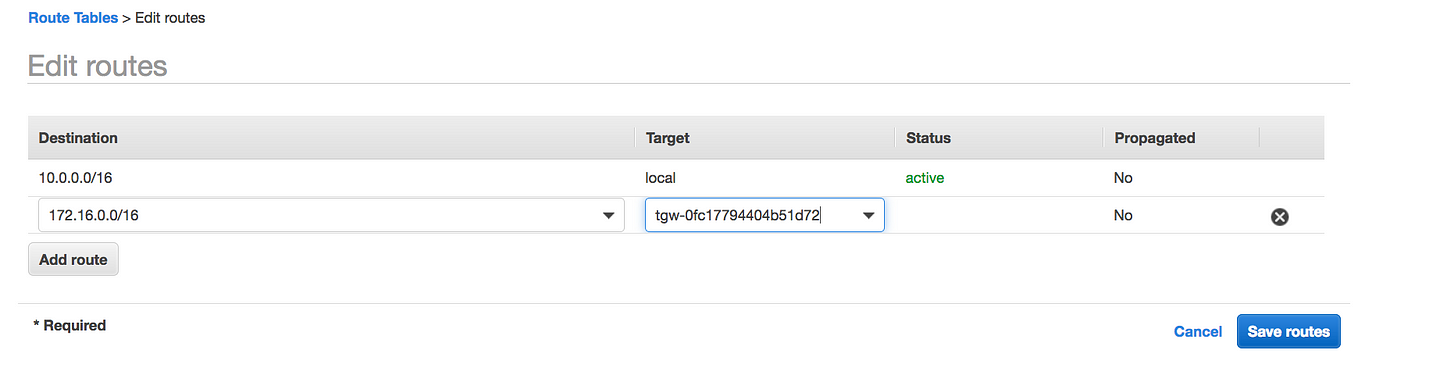
- We need a return path(i.e from our VPC to TGW), VPC1 route table needs to be updated to point to TGW to route to the second VPC and vice-versa(i.e 10.0.0.0/16 to tgw on the second VPC)
# Adding Route for Transit Gateway
resource "aws_route" "my-tgw-route" {
route_table_id = "${aws_route_table.public_route.id}"
destination_cidr_block = "0.0.0.0/0"
transit_gateway_id = "${var.transit_gateway}"
}NOTE: In the AWS Console I am using 172.16.0.0/16 but in terraform code I am using 0.0.0.0/0
Some Key Terms
- associations — Each attachment is associated with exactly one route table. Each route table can be associated with zero to many attachments.
- route propagation — A VPC or VPN connection can dynamically propagate routes to a transit gateway route table.
GitHub Link: https://github.com/100daysofdevops/21_days_of_aws_using_terraform/tree/master/transit_gateway
- Website: https://100daysofdevops.com/
- Twitter: @100daysofdevops OR @lakhera2015
- Facebook: https://www.facebook.com/groups/795382630808645/
- Medium: https://medium.com/@devopslearning
- GitHub: https://github.com/100daysofdevops/100daysofdevops
- Slack: https://join.slack.com/t/100daysofdevops/shared_invite/enQtNzg1MjUzMzQzMzgxLWM4Yjk0ZWJiMjY4ZWE3ODBjZjgyYTllZmUxNzFkNTgxZjQ4NDlmZjkzODAwNDczOTYwOTM2MzlhZDNkM2FkMDA
- YouTube Channel: https://www.youtube.com/user/laprashant/videos?view_as=subscriber
