Welcome to Day 16 of 21 Days of AWS using Terraform. The topic for today is Introduction to AWS Config using Terraform.
What Is AWS Config?
AWS Config provides a detailed view of the configuration of AWS resources in your AWS account. This includes how the resources are related to one another and how they were configured in the past so that you can see how the configurations and relationships change over time.
Features
- Track state of all resources(OS level too — Windows/Linux)
- Meet your compliance need(PCI-DSS, HIPAA)
- Validate against AWS Config Rule
Setting up AWS Config
- Go to AWS Config https://us-west-2.console.aws.amazon.com/config → Get started
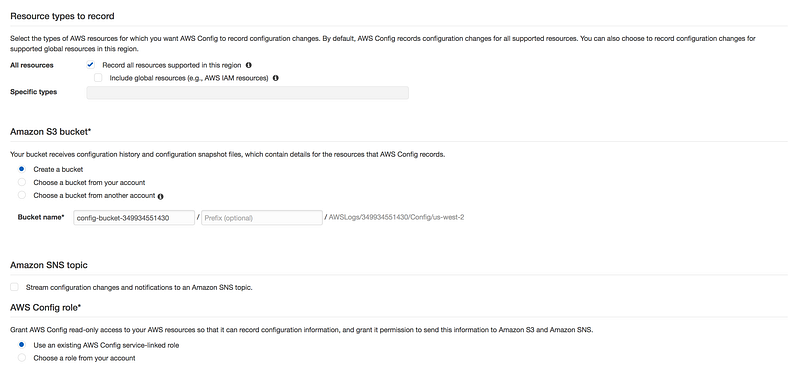
* All resources: You can check on, Record all rsources supported in this region
OR
Global resources like IAM
OR
We can even check specific resources eg: EC2
* Amazin S3 bucket: This bucket will recieve configuration history and configuration snapshot files
* Amazon SNS topic(Optional): We can send config changes to S3 bucket
* AWS Config role: It give AWS config read-only access(IAM Role)to AWS resource
* Skip this for the time being
- Confirm and AWS Config setup for us.
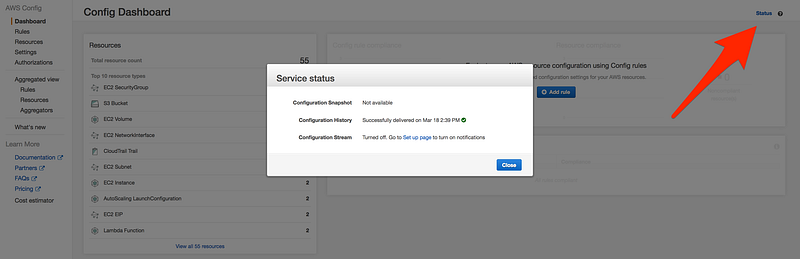
- Check the status of AWS config, by click on the status icon on the top of the page
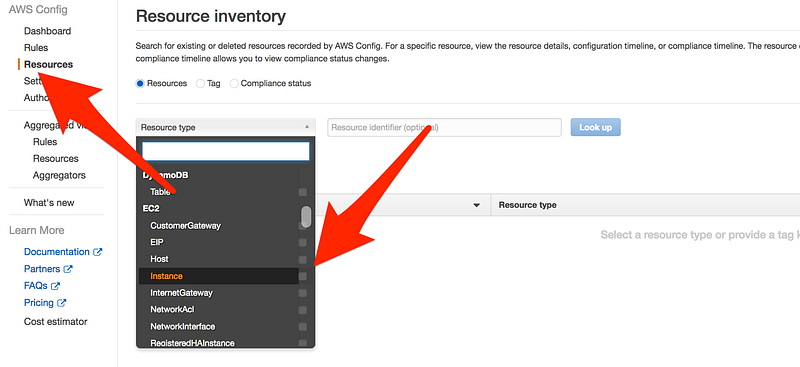
- Now click on Resource and then Instance
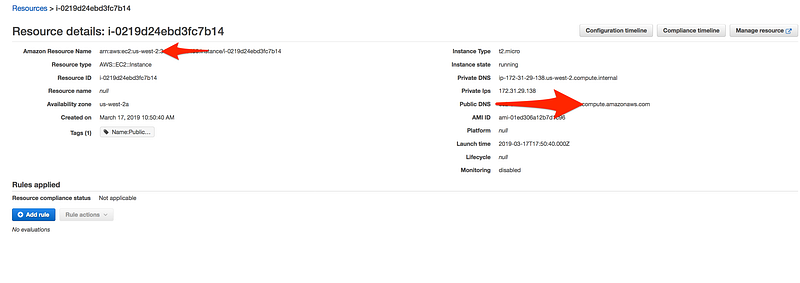
- Click on the Configuration timeline
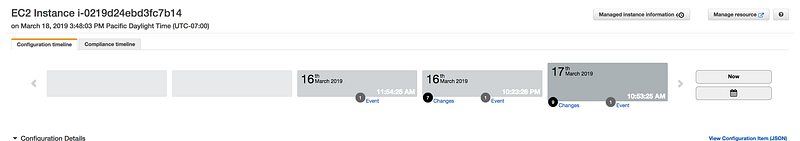
- Scroll down and click on changes
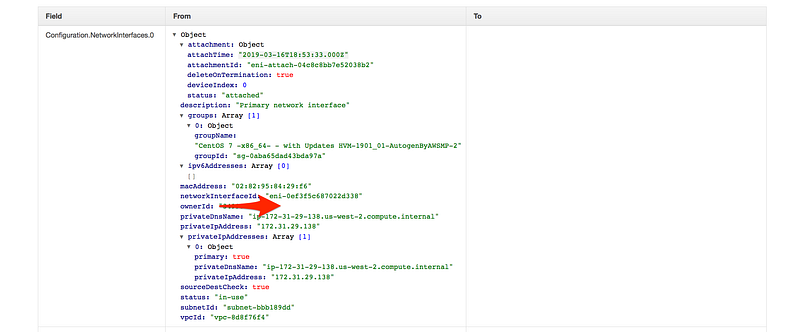
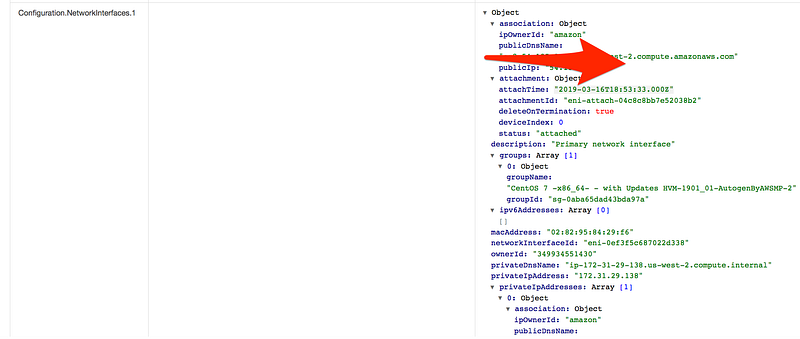
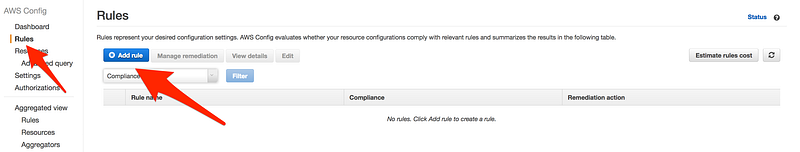
Scenario: Last time we skipped the rule section, this time let add all the config rule, our task for today to make sure for an account is compliant
- CloudTrail must be enabled
- S3 bucket versioning must be enabled
- EC2 instance must be a part of VPC
- We are only using instance type as t2.micro
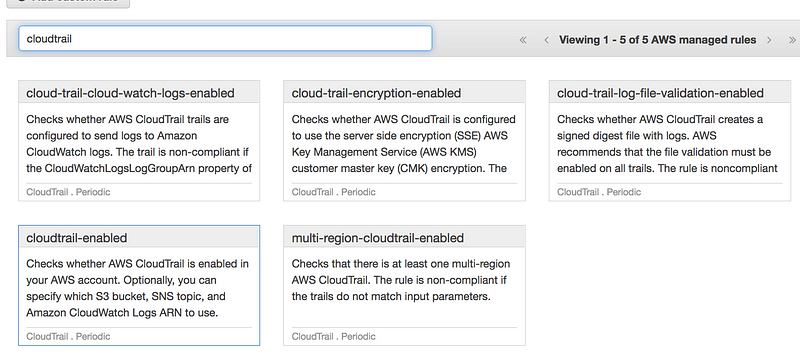
Search for CloudTrail and select cloudtrail-enabled
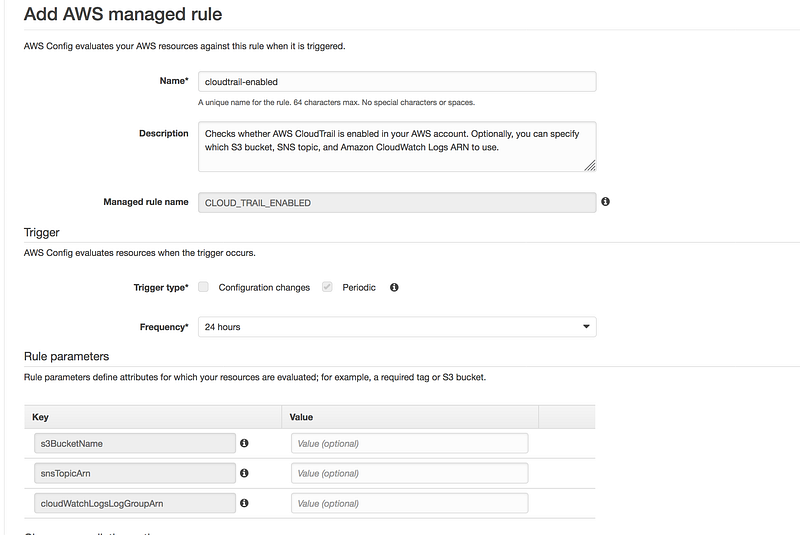
- You don’t need to change any of the default value and click on save
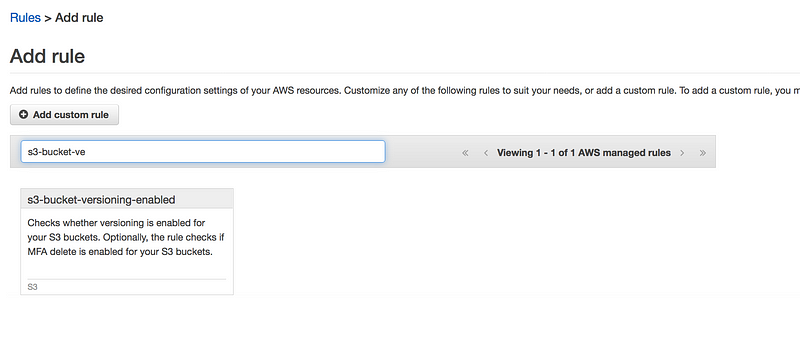
Same way search for S3 bucket versioning enabled
Search for ec2-instances-in-vpc
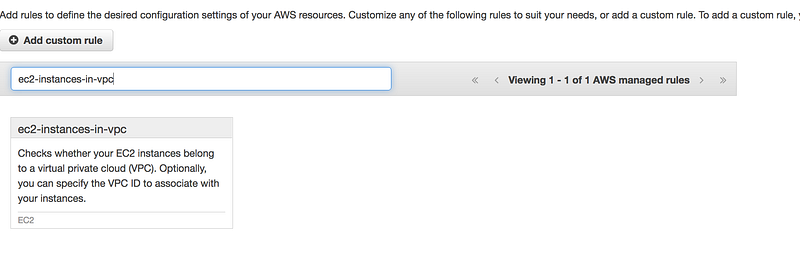
- This requires some changes as you need to specify your VPC id

Search for desired-instance-type
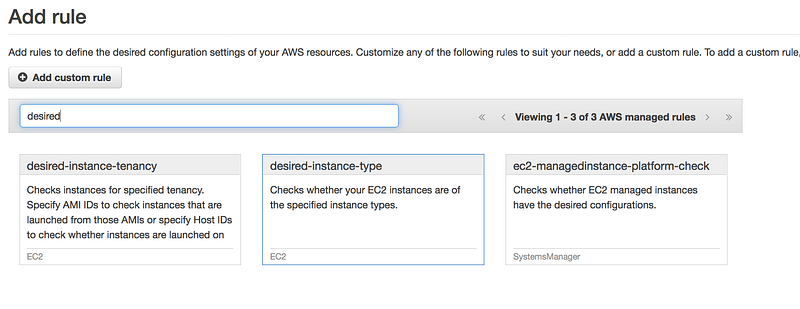
- Add the instanceType Value to t2.micro
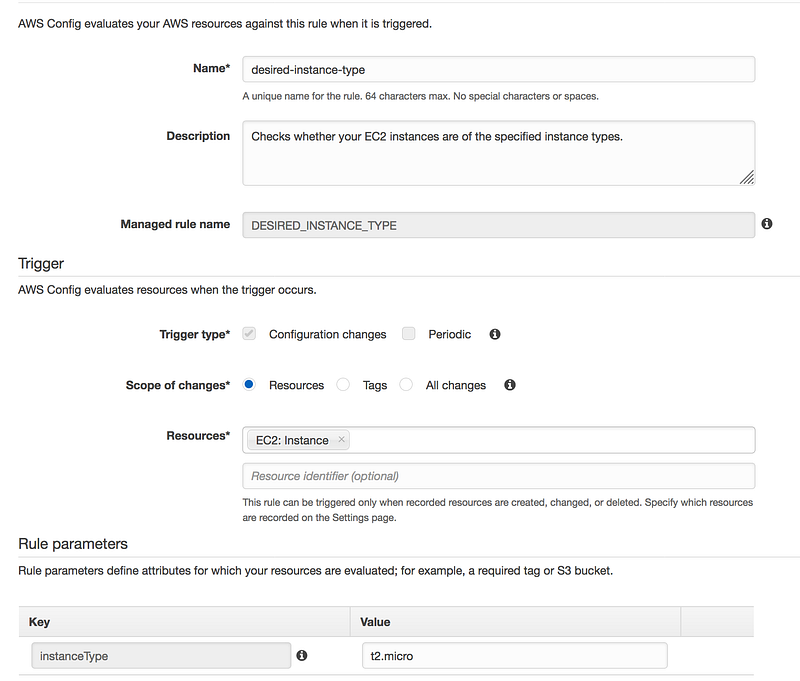
- Finally, you will see something like this
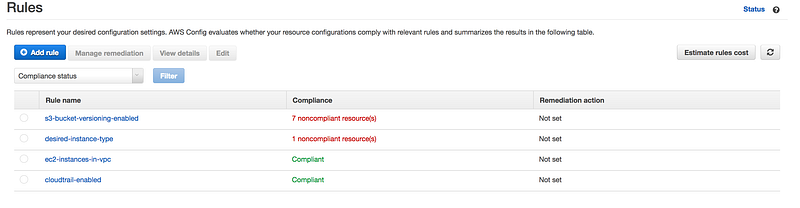
- If you further drill down, as you can see this instance is using t2.medium while in config rule for the desired-instance-type we choose t2.micro
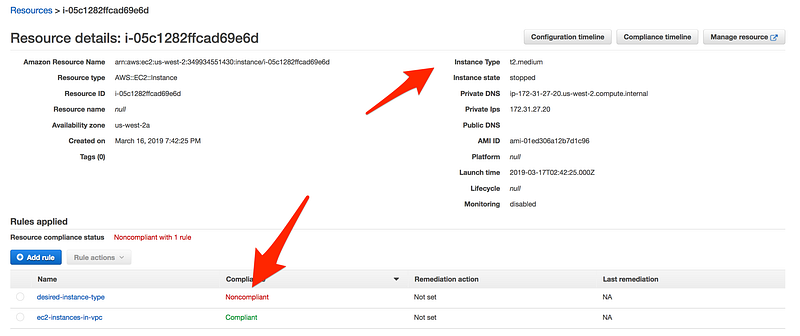
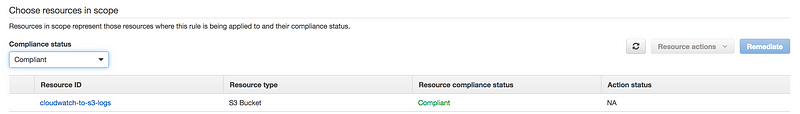
- One more example, as you can see in this case S3 bucket is non-compliant
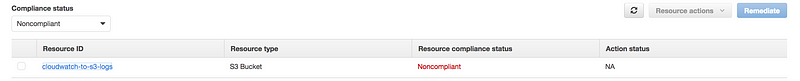
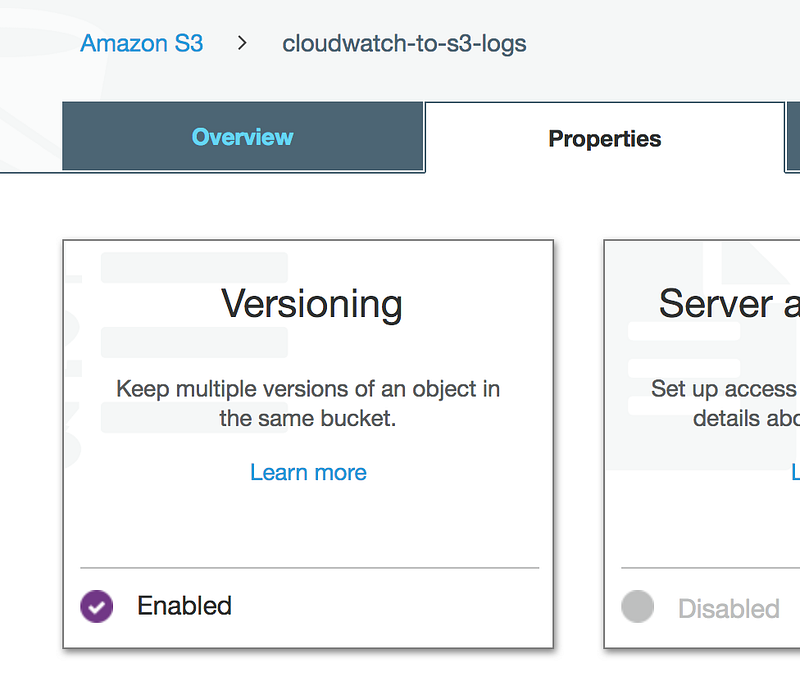
- If we can go to the S3 bucket and enabled versioning
- As we remediated the issue, to see the immediate effect
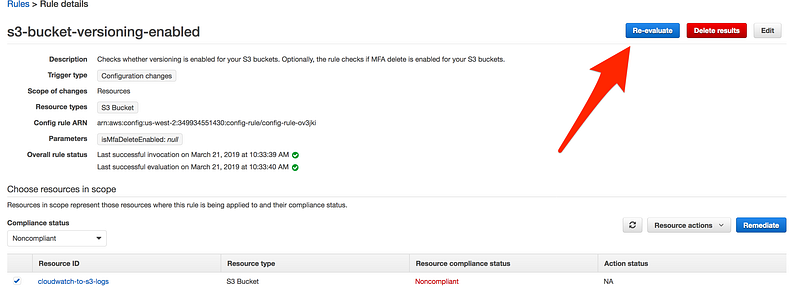
- We are back in business
Terraform Code
- Now we need to automate the entire process and then is no better tool other then terraform to do a job for us.
Terraform Example
provider "aws" {
region = "us-west-2"
}
resource "aws_iam_role" "my-config" {
name = "config-example"
assume_role_policy = <<POLICY
{
"Version": "2012-10-17",
"Statement": [
{
"Action": "sts:AssumeRole",
"Principal": {
"Service": "config.amazonaws.com"
},
"Effect": "Allow",
"Sid": ""
}
]
}
POLICY
}
resource "aws_iam_role_policy_attachment" "my-config" {
role = "${aws_iam_role.my-config.name}"
policy_arn = "arn:aws:iam::aws:policy/service-role/AWSConfigRole"
}
resource "aws_s3_bucket" "my-config" {
bucket = "config-bucket-for-my-test-project"
acl = "private"
versioning {
enabled = true
}
lifecycle {
prevent_destroy = true
}
}
resource "aws_config_configuration_recorder" "my-config" {
name = "config-example"
role_arn = "${aws_iam_role.my-config.arn}"
recording_group {
all_supported = true
include_global_resource_types = true
}
}
resource "aws_config_delivery_channel" "my-config" {
name = "config-example"
s3_bucket_name = "${aws_s3_bucket.my-config.bucket}"
depends_on = ["aws_config_configuration_recorder.my-config"]
}
resource "aws_config_configuration_recorder_status" "config" {
name = "${aws_config_configuration_recorder.my-config.name}"
is_enabled = true
depends_on = ["aws_config_delivery_channel.my-config"]
}
resource "aws_config_config_rule" "instances_in_vpc" {
name = "instances_in_vpc"
source {
owner = "AWS"
source_identifier = "INSTANCES_IN_VPC"
}
depends_on = ["aws_config_configuration_recorder.my-config"]
}
resource "aws_config_config_rule" "cloud_trail_enabled" {
name = "cloud_trail_enabled"
source {
owner = "AWS"
source_identifier = "CLOUD_TRAIL_ENABLED"
}
input_parameters = <<EOF
{
"s3BucketName": "cloudwatch-to-s3-logs"
}
EOF
depends_on = ["aws_config_configuration_recorder.my-config"]
}
resource "aws_config_config_rule" "s3_bucket_versioning_enabled" {
name = "s3_bucket_versioning_enabled"
source {
owner = "AWS"
source_identifier = "S3_BUCKET_VERSIONING_ENABLED"
}
depends_on = ["aws_config_configuration_recorder.my-config"]
}
resource "aws_config_config_rule" "desired_instance_type" {
name = "desired_instance_type"
"source" {
owner = "AWS"
source_identifier = "DESIRED_INSTANCE_TYPE"
}
input_parameters = <<EOF
{
"alarmActionRequired" : "t2.micro"
}
EOF
depends_on = ["aws_config_configuration_recorder.my-config"]
}GitHub Link
https://github.com/100daysofdevops/21_days_of_aws_using_terraform/tree/master/config
Please join me with my journey by following any of the below link
- Website: https://100daysofdevops.com/
- Twitter: @100daysofdevops OR @lakhera2015
- Facebook: https://www.facebook.com/groups/795382630808645/
- Medium: https://medium.com/@devopslearning
- GitHub: https://github.com/100daysofdevops/100daysofdevops
- Slack: https://join.slack.com/t/100daysofdevops/shared_invite/enQtNzg1MjUzMzQzMzgxLWM4Yjk0ZWJiMjY4ZWE3ODBjZjgyYTllZmUxNzFkNTgxZjQ4NDlmZjkzODAwNDczOTYwOTM2MzlhZDNkM2FkMDA
- YouTube Channel: https://www.youtube.com/user/laprashant/videos?view_as=subscriber

Thanks for this post, I am a big big fan of this site would like to go along updated.
Thanks oprol