Welcome to Day 4 of 21 Days of AWS using Terraform, So far we build VPC and EC2, let’s build Application Load Balancer and add two instances behind it. This is going to be a modular approach i.e we are going to get vpc id,subnet1 and subnet2 created during the VPC module and instance id from EC2 module.
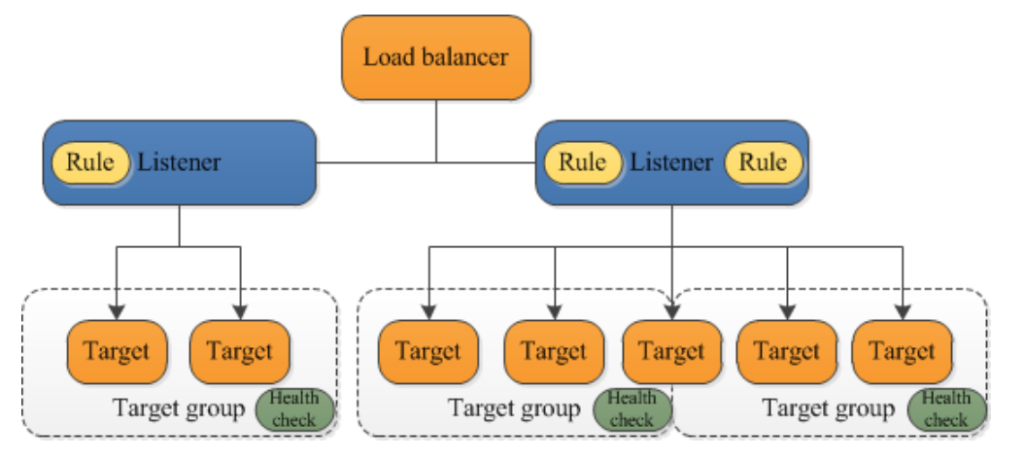
What is the Application Load Balancer?
The Application Load Balancer is a feature of ElasticLoad Balancing that allows a developer to configure and route incoming end-user traffic to applications based in the Amazon Web Services (AWS) public cloud.
Features
- Layer7 load balancer(HTTP and HTTPs traffic)
- Support Path and Host-based routing(which let you route traffic to different target group)
- Listener support IPv6
Some Key Terms
Target Group
Target types:
- Instance types: Route traffic to the Primary Private IP address of that Instance
- IP: Route traffic to a specified IP address
- Lambda function
Health Check
- Determines whether to send traffic to a given instance
- Each instance must pass its a health check
- Sends HTTP GET request and looks for a specific response/success code
https://docs.aws.amazon.com/elasticloadbalancing/latest/application/introduction.html
Step1: Define the target group: This is going to provide a resource for use with Load Balancer.
resource "aws_lb_target_group" "my-target-group" {
health_check {
interval = 10
path = "/"
protocol = "HTTP"
timeout = 5
healthy_threshold = 5
unhealthy_threshold = 2
}
name = "my-test-tg"
port = 80
protocol = "HTTP"
target_type = "instance"
vpc_id = "${var.vpc_id}"
}health_check: Your Application Load Balancer periodically sends requests to its registered targets to test their status. These tests are called health checks interval: The approximate amount of time, in seconds, between health checks of an individual target. Minimum value 5 seconds, Maximum value 300 seconds. Default 30 seconds. path: The destination for the health check request protocol: The protocol to use to connect with the target. Defaults to HTTP timeout:The amount of time, in seconds, during which no response means a failed health check. For Application Load Balancers, the range is 2 to 60 seconds and the default is 5 seconds healthy_threshold: The number of consecutive health checks successes required before considering an unhealthy target healthy. Defaults to 3. unhealthy_threshold: The number of consecutive health check failures required before considering the target unhealthy matcher: The HTTP codes to use when checking for a successful response from a target. You can specify multiple values (for example, "200,202") or a range of values (for example, "200-299")name: The name of the target group. If omitted, Terraform will assign a random, unique name. port: The port on which targets receive traffic protocol: The protocol to use for routing traffic to the targets. Should be one of "TCP", "TLS", "HTTP" or "HTTPS". Required when target_type is instance or ip vpc_id:The identifier of the VPC in which to create the target group. This value we will get from the VPC module we built earlier target_type: The type of target that you must specify when registering targets with this target group.Possible values instance id, ip address
- The VPC module we built earlier, we need to modify it a little built by outputting the value of VPC id(outputs.tf) which will act as an input to Application Load Balancer Module
output "vpc_id" {
value = "${aws_vpc.main.id}"
}Step2: Provides the ability to register instances with an Application Load Balancer (ALB)
resource "aws_lb_target_group_attachment" "my-alb-target-group-attachment1" {
target_group_arn = "${aws_lb_target_group.my-target-group.arn}"
target_id = "${var.instance1_id}"
port = 80
}
resource "aws_lb_target_group_attachment" "my-alb-target-group-attachment2" {
target_group_arn = "${aws_lb_target_group.my-target-group.arn}"
target_id = "${var.instance2_id}"
port = 80
}target_group_arn: The ARN of the target group with which to register targets
target_id: The ID of the target. This is the Instance ID for an instance. We will get this value from EC2 module
port: The port on which targets receive traffic.
- We need to modify the EC2 module(outputs.tf) by outputting the value of EC2 id which will act as an input to Application Load Balancer Module
output "instance1_id" {
value = "${element(aws_instance.my-test-instance.*.id, 1)}"
}
output "instance2_id" {
value = "${element(aws_instance.my-test-instance.*.id, 2)}"
}element(list, index)– Returns a single element from a list at the given index. If the index is greater than the number of elements, this function will wrap using a standard mod algorithm. This function only works on flat lists.
https://www.terraform.io/docs/configuration-0-11/interpolation.html#element-list-index-
Step3: Define the load balancer
resource "aws_lb" "my-aws-alb" {
name = "my-test-alb"
internal = false
security_groups = [
"${aws_security_group.my-alb-sg.id}",
]
subnets = [
"${var.subnet1}",
"${var.subnet2}",
]
tags = {
Name = "my-test-alb"
}
ip_address_type = "ipv4"
load_balancer_type = "application"
}name: The name of the LB. This name must be unique within your AWS account, can have a maximum of 32 characters, must contain only alphanumeric characters or hyphens, and must not begin or end with a hyphen. If not specified, Terraform will autogenerate a name beginning with tf-lb (This part is important as Terraform auto
internal: If true, the LB will be internal.
load_balancer_type: The type of load balancer to create. Possible values are application or network. The default value is the application.
ip_address_type: The type of IP addresses used by the subnets for your load balancer. The possible values are ipv4 and dualstack
subnets: A list of subnet IDs to attach to the LB. In this case, I am attaching two public subnets we created during load balancer creation. This value we will get out from the VPC module.
tags: A mapping of tags to assign to the resource.
- We need to modify the VPC module and output the value of two subnet id which will act as an input to application load balancer module
output "subnet1" {
value = "${element(aws_subnet.public_subnet.*.id, 1 )}"
}
output "subnet2" {
value = "${element(aws_subnet.public_subnet.*.id, 2 )}"
}Step4: Security group used by ALB
resource "aws_security_group" "my-alb-sg" {
name = "my-alb-sg"
vpc_id = "${var.vpc_id}"
}
resource "aws_security_group_rule" "inbound_ssh" {
from_port = 22
protocol = "tcp"
security_group_id = "${aws_security_group.my-alb-sg.id}"
to_port = 22
type = "ingress"
cidr_blocks = ["0.0.0.0/0"]
}
resource "aws_security_group_rule" "inbound_http" {
from_port = 80
protocol = "tcp"
security_group_id = "${aws_security_group.my-alb-sg.id}"
to_port = 80
type = "ingress"
cidr_blocks = ["0.0.0.0/0"]
}
resource "aws_security_group_rule" "outbound_all" {
from_port = 0
protocol = "-1"
security_group_id = "${aws_security_group.my-alb-sg.id}"
to_port = 0
type = "egress"
cidr_blocks = ["0.0.0.0/0"]
}NOTE: I already explained about Security Group in the VPC module.
Step5: Provides a Load Balancer Listener resource
resource "aws_lb_listener" "my-test-alb-listner" {
load_balancer_arn = "${aws_lb.my-aws-alb.arn}"
port = 80
protocol = "HTTP"
default_action {
type = "forward"
target_group_arn = "${aws_lb_target_group.my-target-group.arn}"
}
}load_balancer_arn – The ARN of the load balancer(we created in step3)
port – (Required) The port on which the load balancer is listening.
protocol – (Optional) The protocol for connections from clients to the load balancer. Valid values are TCP, TLS, UDP, TCP_UDP, HTTP and HTTPS. Defaults to HTTP.
default_action – An Action block.
type – (Required) The type of routing action. Valid values forward, redirect, fixed-response, authenticate-cognito and authenticate-oidc.
target_group_arn – The ARN of the Target Group to which to route traffic. Required if type is forward(Created in Step1)
Final Code
provider "aws" {
region = "us-west-2"
}
resource "aws_lb_target_group" "my-target-group" {
health_check {
interval = 10
path = "/"
protocol = "HTTP"
timeout = 5
healthy_threshold = 5
unhealthy_threshold = 2
}
name = "my-test-tg"
port = 80
protocol = "HTTP"
target_type = "instance"
vpc_id = "${var.vpc_id}"
}
resource "aws_lb_target_group_attachment" "my-alb-target-group-attachment1" {
target_group_arn = "${aws_lb_target_group.my-target-group.arn}"
target_id = "${var.instance1_id}"
port = 80
}
resource "aws_lb_target_group_attachment" "my-alb-target-group-attachment2" {
target_group_arn = "${aws_lb_target_group.my-target-group.arn}"
target_id = "${var.instance2_id}"
port = 80
}
resource "aws_lb" "my-aws-alb" {
name = "my-test-alb"
internal = false
security_groups = [
"${aws_security_group.my-alb-sg.id}",
]
subnets = [
"${var.subnet1}",
"${var.subnet2}",
]
tags = {
Name = "my-test-alb"
}
ip_address_type = "ipv4"
load_balancer_type = "application"
}
resource "aws_lb_listener" "my-test-alb-listner" {
load_balancer_arn = "${aws_lb.my-aws-alb.arn}"
port = 80
protocol = "HTTP"
default_action {
type = "forward"
target_group_arn = "${aws_lb_target_group.my-target-group.arn}"
}
}
resource "aws_security_group" "my-alb-sg" {
name = "my-alb-sg"
vpc_id = "${var.vpc_id}"
}
resource "aws_security_group_rule" "inbound_ssh" {
from_port = 22
protocol = "tcp"
security_group_id = "${aws_security_group.my-alb-sg.id}"
to_port = 22
type = "ingress"
cidr_blocks = ["0.0.0.0/0"]
}
resource "aws_security_group_rule" "inbound_http" {
from_port = 80
protocol = "tcp"
security_group_id = "${aws_security_group.my-alb-sg.id}"
to_port = 80
type = "ingress"
cidr_blocks = ["0.0.0.0/0"]
}
resource "aws_security_group_rule" "outbound_all" {
from_port = 0
protocol = "-1"
security_group_id = "${aws_security_group.my-alb-sg.id}"
to_port = 0
type = "egress"
cidr_blocks = ["0.0.0.0/0"]
}
variables.tf
variable "vpc_id" {}
variable "instance1_id" {}
variable "instance2_id" {}
variable "subnet1" {}
variable "subnet2" {}GitHub Link
https://github.com/100daysofdevops/21_days_of_aws_using_terraform/tree/master/alb
Final ALB Module will look like this
module "alb" {
source = "./alb"
vpc_id = "${module.vpc.vpc_id}"
instance1_id = "${module.ec2.instance1_id}"
instance2_id = "${module.ec2.instance2_id}"
subnet1 = "${module.vpc.subnet1}"
subnet2 = "${module.vpc.subnet2}"
}Final Code
https://github.com/100daysofdevops/21_days_of_aws_using_terraform
Looking forward for you guys to join this journey
- Website: https://100daysofdevops.com/
- Twitter: @100daysofdevops OR @lakhera2015
- Facebook: https://www.facebook.com/groups/795382630808645/
- Medium: https://medium.com/@devopslearning
- GitHub: https://github.com/100daysofdevops/100daysofdevops
- Slack: https://join.slack.com/t/100daysofdevops/shared_invite/enQtNzg1MjUzMzQzMzgxLWM4Yjk0ZWJiMjY4ZWE3ODBjZjgyYTllZmUxNzFkNTgxZjQ4NDlmZjkzODAwNDczOTYwOTM2MzlhZDNkM2FkMDA
- YouTube Channel: https://www.youtube.com/user/laprashant/videos?view_as=subscriber
In addition to that, I am going to host 5 meetups whose aim is to build the below architecture.

- Meetup: https://www.meetup.com/100daysofdevops
- Day1(Nov 10): Introduction to Terraform https://www.meetup.com/100daysofdevops/events/266192294/
- Day 2(Nov 16): Building VPC using Terraform
- Day 3(Nov 17): Creating EC2 Instance inside this VPC using Terraform
- Day 4(Nov 23): Adding Application Load Balancer and Auto-Scaling to the EC2 instance created on Day 3
- Day5(Nov 24): Add Backend MySQL Database and CloudWatch Alarm using Terraform
