Welcome to Day 20 of 21 Days of Docker, the topic for today Introduction and Installation of Docker Enterprise Edition
What is Docker Enterprise Edition?
Docker Enterprise Edition (Docker EE) is designed for enterprise development and IT teams who build, ship, and run business-critical applications in production and at scale.
Docker Enterprise Features
- Role-based access control
- LDAP/AD integration
- Image scanning and signing enforcement policies
- Security policies
Universal Control Plane
- Docker Universal Control Plane (UCP) is the enterprise-grade cluster management solution from Docker. You install it on-premises or in your virtual private cloud, and it helps you manage your Docker cluster and applications through a single interface.
Docker Trusted Registry
- Docker Trusted Registry (DTR) is the enterprise-grade image storage solution from Docker. You install it behind your firewall so that you can securely store and manage the Docker images you use in your applications.
Installing Docker Enterprise Edition
Setup
- 3 Ubuntu Hosts
- 1 Universal Control Plane(UCP) manager
- 1 Docker Trusted Registry(DTR)
- 1 Worker Node
- Let take a look, how we can install and configure the Docker EE engine, UCP, and DTR.
- Perform the following steps on all three servers:
- Start a free trial for Docker EE: If you don’t have a Docker EE trial already started, then launch one here: https://hub.docker.com/editions/enterprise/docker-ee-trial. This free trial lasts up to a month, but another one can be started right after it expires.
- Go to https://hub.docker.com/my-content and retrieve a unique URL for Docker EE.
- Click Setup.
- Copy the URL generated for Docker EE.
- Set a few environment variables. Ensure that the unique URL generated for Docker EE is also used here:
DOCKER_EE_URL=<YOUR_DOCKER_EE_URL>
DOCKER_EE_VERSION=18.09- Verify that the required packages install successfully:
$ sudo apt-get install -y \
> apt-transport-https \
> ca-certificates \
> curl \
> software-properties-common
[sudo] password for cloud_user:
Reading package lists... Done
Building dependency tree
Reading state information... Done
ca-certificates is already the newest version (20180409).
curl is already the newest version (7.58.0-2ubuntu3.8).
The following additional packages will be installed:
python3-software-properties
The following NEW packages will be installed:
apt-transport-https
The following packages will be upgraded:
python3-software-properties software-properties-common
2 upgraded, 1 newly installed, 0 to remove and 101 not upgraded.
Need to get 35.3 kB of archives.
After this operation, 166 kB of additional disk space will be used.
Get:1 http://us-east-1.ec2.archive.ubuntu.com/ubuntu bionic-updates/universe amd64 apt-transport-https all 1.6.12 [1692 B]
Get:2 http://us-east-1.ec2.archive.ubuntu.com/ubuntu bionic-updates/main amd64 software-properties-common all 0.96.24.32.11 [9996 B]
Get:3 http://us-east-1.ec2.archive.ubuntu.com/ubuntu bionic-updates/main amd64 python3-software-properties all 0.96.24.32.11 [23.6 kB]
Fetched 35.3 kB in 0s (1949 kB/s)
Selecting previously unselected package apt-transport-https.
(Reading database ... 112422 files and directories currently installed.)
Preparing to unpack .../apt-transport-https_1.6.12_all.deb ...
Unpacking apt-transport-https (1.6.12) ...
Preparing to unpack .../software-properties-common_0.96.24.32.11_all.deb ...
Unpacking software-properties-common (0.96.24.32.11) over (0.96.24.32.7) ...
Preparing to unpack .../python3-software-properties_0.96.24.32.11_all.deb ...
Unpacking python3-software-properties (0.96.24.32.11) over (0.96.24.32.7) ...
Setting up apt-transport-https (1.6.12) ...
Processing triggers for man-db (2.8.3-2ubuntu0.1) ...
Setting up python3-software-properties (0.96.24.32.11) ...
Processing triggers for dbus (1.12.2-1ubuntu1.1) ...
Setting up software-properties-common (0.96.24.32.11) ...- Add the
gpgkey and repository using the unique URL for Docker EE
curl -fsSL "${DOCKER_EE_URL}/ubuntu/gpg" | sudo apt-key add -
OK
$ sudo add-apt-repository \
> "deb [arch=$(dpkg --print-architecture)] $DOCKER_EE_URL/ubuntu \
> $(lsb_release -cs) \
> stable-$DOCKER_EE_VERSION"
Hit:1 http://us-east-1.ec2.archive.ubuntu.com/ubuntu bionic InRelease
Hit:2 http://us-east-1.ec2.archive.ubuntu.com/ubuntu bionic-updates InRelease
Hit:3 http://us-east-1.ec2.archive.ubuntu.com/ubuntu bionic-backports InRelease
Get:4 https://storebits.docker.com/ee/trial/sub-8158a9b3-de4e-4753-b73e-d386fca163ff/ubuntu bionic InRelease [116 kB]
Get:5 http://security.ubuntu.com/ubuntu bionic-security InRelease [88.7 kB]
Get:6 https://storebits.docker.com/ee/trial/sub-8158a9b3-de4e-4753-b73e-d386fca163ff/ubuntu bionic/stable-18.09 amd64 Packages [6386 B]
Fetched 211 kB in 0s (454 kB/s)
Reading package lists... Done- Install Docker EE:
$ sudo apt-get update
Hit:1 http://us-east-1.ec2.archive.ubuntu.com/ubuntu bionic InRelease
Hit:2 http://us-east-1.ec2.archive.ubuntu.com/ubuntu bionic-updates InRelease
Hit:3 http://us-east-1.ec2.archive.ubuntu.com/ubuntu bionic-backports InRelease
Hit:4 https://storebits.docker.com/ee/trial/sub-8158a9b3-de4e-4753-b73e-d386fca163ff/ubuntu bionic InRelease
Get:5 http://security.ubuntu.com/ubuntu bionic-security InRelease [88.7 kB]
Fetched 88.7 kB in 1s (166 kB/s)
Reading package lists... Done
$ sudo apt-get install -y docker-ee=5:18.09.4~3-0~ubuntu-bionic
Reading package lists... Done
Building dependency tree
Reading state information... Done
The following additional packages will be installed:
aufs-tools cgroupfs-mount containerd.io docker-ee-cli libltdl7 pigz
The following NEW packages will be installed:
aufs-tools cgroupfs-mount containerd.io docker-ee docker-ee-cli libltdl7 pigz
0 upgraded, 7 newly installed, 0 to remove and 101 not upgraded.
Need to get 56.5 MB of archives.
After this operation, 266 MB of additional disk space will be used.
Get:1 http://us-east-1.ec2.archive.ubuntu.com/ubuntu bionic/universe amd64 pigz amd64 2.4-1 [57.4 kB]
Get:2 http://us-east-1.ec2.archive.ubuntu.com/ubuntu bionic/universe amd64 aufs-tools amd64 1:4.9+20170918-1ubuntu1 [104 kB]
Get:3 http://us-east-1.ec2.archive.ubuntu.com/ubuntu bionic/universe amd64 cgroupfs-mount all 1.4 [6320 B]
Get:4 http://us-east-1.ec2.archive.ubuntu.com/ubuntu bionic/main amd64 libltdl7 amd64 2.4.6-2 [38.8 kB]
Get:5 https://storebits.docker.com/ee/trial/sub-8158a9b3-de4e-4753-b73e-d386fca163ff/ubuntu bionic/stable-18.09 amd64 containerd.io amd64 1.2.5-1 [19.9 MB]
Get:6 https://storebits.docker.com/ee/trial/sub-8158a9b3-de4e-4753-b73e-d386fca163ff/ubuntu bionic/stable-18.09 amd64 docker-ee-cli amd64 5:18.09.10~3-0~ubuntu-bionic [17.1 MB]
Get:7 https://storebits.docker.com/ee/trial/sub-8158a9b3-de4e-4753-b73e-d386fca163ff/ubuntu bionic/stable-18.09 amd64 docker-ee amd64 5:18.09.4~3-0~ubuntu-bionic [19.3 MB]
Fetched 56.5 MB in 2s (30.9 MB/s)
Selecting previously unselected package pigz.
(Reading database ... 112428 files and directories currently installed.)
Preparing to unpack .../0-pigz_2.4-1_amd64.deb ...
Unpacking pigz (2.4-1) ...
Selecting previously unselected package aufs-tools.
Preparing to unpack .../1-aufs-tools_1%3a4.9+20170918-1ubuntu1_amd64.deb ...
Unpacking aufs-tools (1:4.9+20170918-1ubuntu1) ...
Selecting previously unselected package cgroupfs-mount.
Preparing to unpack .../2-cgroupfs-mount_1.4_all.deb ...
Unpacking cgroupfs-mount (1.4) ...
Selecting previously unselected package containerd.io.
Preparing to unpack .../3-containerd.io_1.2.5-1_amd64.deb ...
Unpacking containerd.io (1.2.5-1) ...
Selecting previously unselected package docker-ee-cli.
Preparing to unpack .../4-docker-ee-cli_5%3a18.09.10~3-0~ubuntu-bionic_amd64.deb ...
Unpacking docker-ee-cli (5:18.09.10~3-0~ubuntu-bionic) ...
Selecting previously unselected package docker-ee.
Preparing to unpack .../5-docker-ee_5%3a18.09.4~3-0~ubuntu-bionic_amd64.deb ...
Unpacking docker-ee (5:18.09.4~3-0~ubuntu-bionic) ...
Selecting previously unselected package libltdl7:amd64.
Preparing to unpack .../6-libltdl7_2.4.6-2_amd64.deb ...
Unpacking libltdl7:amd64 (2.4.6-2) ...
Setting up aufs-tools (1:4.9+20170918-1ubuntu1) ...
Setting up containerd.io (1.2.5-1) ...
Created symlink /etc/systemd/system/multi-user.target.wants/containerd.service → /lib/systemd/system/containerd.service.
Processing triggers for ureadahead (0.100.0-20) ...
Setting up cgroupfs-mount (1.4) ...
Processing triggers for libc-bin (2.27-3ubuntu1) ...
Setting up docker-ee-cli (5:18.09.10~3-0~ubuntu-bionic) ...
Processing triggers for systemd (237-3ubuntu10.29) ...
Setting up libltdl7:amd64 (2.4.6-2) ...
Setting up docker-ee (5:18.09.4~3-0~ubuntu-bionic) ...
Created symlink /etc/systemd/system/multi-user.target.wants/docker.service → /lib/systemd/system/docker.service.
Created symlink /etc/systemd/system/sockets.target.wants/docker.socket → /lib/systemd/system/docker.socket.
Processing triggers for man-db (2.8.3-2ubuntu0.1) ...
Setting up pigz (2.4-1) ...
Processing triggers for ureadahead (0.100.0-20) ...
Processing triggers for libc-bin (2.27-3ubuntu1) ...- Add user access to run the Docker commands
$ sudo usermod -a -G docker centosNOTE: You need to resource your env back or just logout and log back in
- Test the Docker EE installation to verify that it’s working:
$ docker version
Client:
Version: 18.09.10
API version: 1.39
Go version: go1.12.10
Git commit: 2408617bbf
Built: Fri Oct 4 20:56:49 2019
OS/Arch: linux/amd64
Experimental: false
Server: Docker Engine - Enterprise
Engine:
Version: 18.09.4
API version: 1.39 (minimum version 1.12)
Go version: go1.10.8
Git commit: c3516c4
Built: Wed Mar 27 18:02:16 2019
OS/Arch: linux/amd64
Experimental: falseSet Up the UCP Manager
- With docker installation out of the way, let install UCP manager on UCP manager host
- Pull the UCP image:
$ docker image pull docker/ucp:3.1.5
3.1.5: Pulling from docker/ucp
cd784148e348: Pull complete
3871e7d70c20: Pull complete
b7a92b3565bc: Pull complete
Digest: sha256:334d7b21e30d7b3caeea6dd0fb4e79633b7035a4fd63ea479dfac19470206012
Status: Downloaded newer image for docker/ucp:3.1.5- Use the UCP image for the installation:
$ docker container run --rm -it --name ucp \
> -v /var/run/docker.sock:/var/run/docker.sock \
> docker/ucp:3.1.5 install \
> --host-address 10.0.1.101 \
> --interactive
INFO[0000] Your engine version 18.09.4, build c3516c4 (4.15.0-1034-aws) is compatible with UCP 3.1.5 (e3b1ac1)
Admin Username: admin <--- Provide a username
Admin Password: <-- and a password
Confirm Admin Password:
INFO[0014] Pulling required images... (this may take a while)
INFO[0014] Pulling docker/ucp-dsinfo:3.1.5
INFO[0022] Pulling docker/ucp-cfssl:3.1.5
INFO[0022] Pulling docker/ucp-interlock-extension:3.1.5
INFO[0023] Pulling docker/ucp-agent:3.1.5
INFO[0024] Pulling docker/ucp-calico-node:3.1.5
INFO[0027] Pulling docker/ucp-compose:3.1.5
INFO[0028] Pulling docker/ucp-kube-compose-api:3.1.5
INFO[0029] Pulling docker/ucp-kube-dns:3.1.5
INFO[0030] Pulling docker/ucp-etcd:3.1.5
INFO[0031] Pulling docker/ucp-kube-dns-dnsmasq-nanny:3.1.5
INFO[0033] Pulling docker/ucp-interlock:3.1.5
INFO[0033] Pulling docker/ucp-auth:3.1.5
INFO[0034] Pulling docker/ucp-hyperkube:3.1.5
INFO[0042] Pulling docker/ucp-controller:3.1.5
INFO[0045] Pulling docker/ucp-auth-store:3.1.5
INFO[0046] Pulling docker/ucp-metrics:3.1.5
INFO[0049] Pulling docker/ucp-interlock-proxy:3.1.5
INFO[0050] Pulling docker/ucp-pause:3.1.5
INFO[0050] Pulling docker/ucp-swarm:3.1.5
INFO[0051] Pulling docker/ucp-kube-compose:3.1.5
INFO[0052] Pulling docker/ucp-kube-dns-sidecar:3.1.5
INFO[0053] Pulling docker/ucp-calico-cni:3.1.5
INFO[0055] Pulling docker/ucp-calico-kube-controllers:3.1.5
INFO[0060] Pulling docker/ucp-azure-ip-allocator:3.1.5
WARN[0061] None of the hostnames we'll be using in the UCP certificates [ip-10-0-1-101 127.0.0.1 172.17.0.1 10.0.1.101] contain a domain component. Your generated certs may fail TLS validation unless you only use one of these shortnames or IPs to connect. You can use the --san flag to add more aliases
You may enter additional aliases (SANs) now or press enter to proceed with the above list.
Additional aliases: <-- Hit enter and select default aliases
INFO[0000] Initializing a new swarm at 10.0.1.101
INFO[0013] Installing UCP with host address 10.0.1.101 - If this is incorrect, please specify an alternative address with the '--host-address' flag
INFO[0013] Deploying UCP Service...
INFO[0089] Installation completed on ip-10-0-1-101 (node kwropkch0bblk0ua5ld7gezco)
INFO[0089] UCP Instance ID: 9wbsl1mze4aiqy1k9h6s7h98q
INFO[0089] UCP Server SSL: SHA-256 Fingerprint=40:72:CC:57:89:C0:83:1E:42:28:7B:B8:23:AE:A5:A5:7D:AA:FF:2A:EC:F7:36:DD:08:79:7E:70:29:17:2B:A6
INFO[0089] Login to UCP at https://10.0.1.101:443
INFO[0089] Username: admin
INFO[0089] Password: (your admin password)- In a web browser go to:
https://[UCP manager Public IP]for accessing the UCP manager
- Use the admin credentials that were created during the initial setup process to log in.
- Note: A warning about the self-signed certificate’s validity may emerge. This notification can be disregarded
- Go to the Docker site: https://hub.docker.com/my-content to retrieve the license file.
Add Both UCP Workers to the Cluster
- Navigate back to the UCP manager interface in a web browser to retrieve the worker
joincommand. We will also generate adocker swarm joincommand that can be copied. - Click Shared Resources
- Click Nodes
- Click Add Node.
- Apply the following values on the Add Node page:
- Node type: Linux
- Node role: Worker
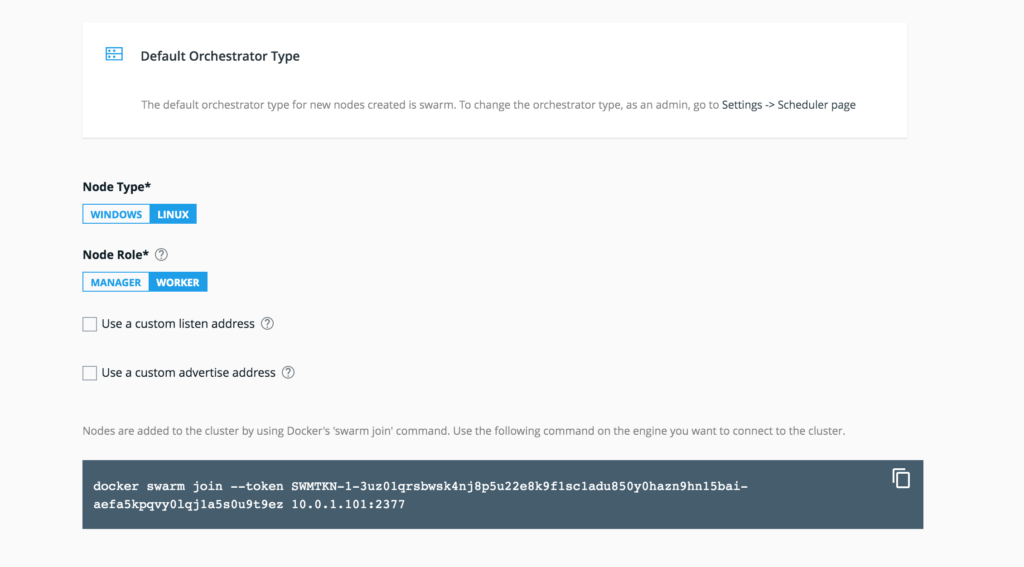
$ docker swarm join --token SWMTKN-1-3uz01qrsbwsk4nj8p5u22e8k9f1sc1adu850y0hazn9hn15bai-aefa5kpqvy0lqj1a5s0u9t9ez 10.0.1.101:2377
This node joined a swarm as a worker.
$ docker swarm join --token SWMTKN-1-3uz01qrsbwsk4nj8p5u22e8k9f1sc1adu850y0hazn9hn15bai-aefa5kpqvy0lqj1a5s0u9t9ez 10.0.1.101:2377
This node joined a swarm as a worker.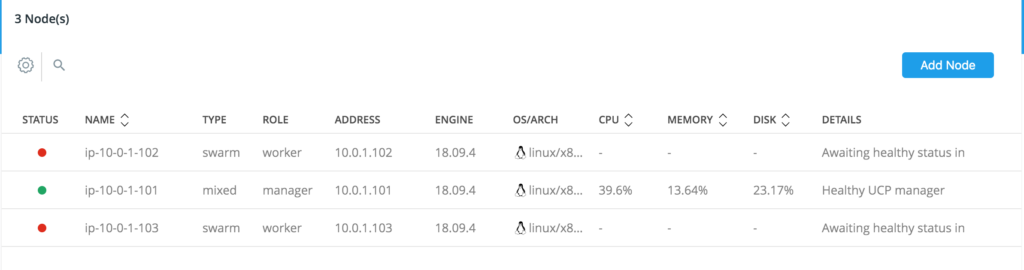
Set Up Docker Trusted Registry
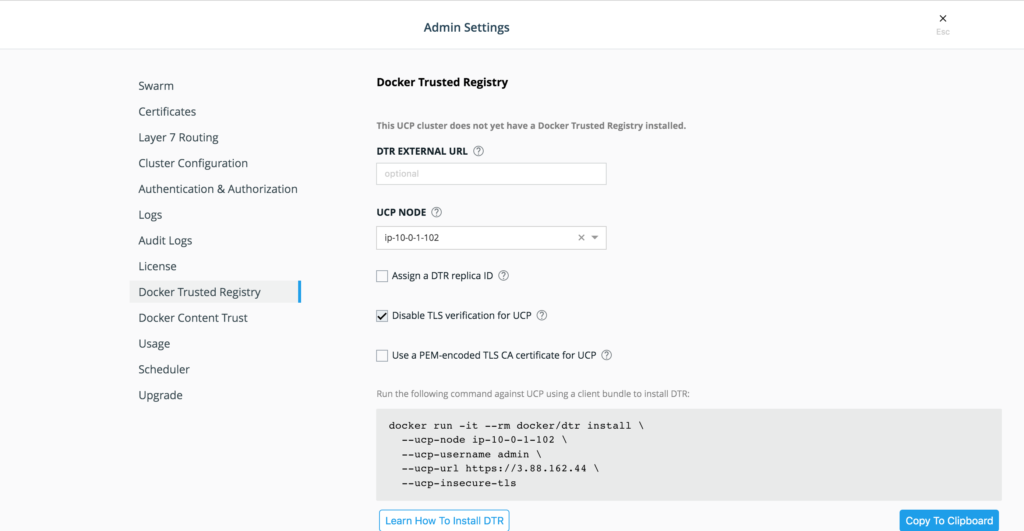
Get the DTR setup command from the UCP manager by performing the following steps:
- Access the UCP manager from a web browser.
- Click Admin > Admin Settings.
- Click Docker Trusted Registry.
- On the Admin Settings page locate the UCP Node section.
- Click ip-10-0-1-102.
- Click the checkbox labeled Disable TLS verification for UCP.
$ docker run -it --rm docker/dtr install --ucp-node ip-10-0-1-102 --ucp-username admin --ucp-url https://10.0.1.101 --ucp-insecure-tls
Unable to find image 'docker/dtr:latest' locally
latest: Pulling from docker/dtr
9d48c3bd43c5: Pull complete
dcfa06138f1d: Pull complete
3a8b460c24c5: Pull complete
4bb8be37e77e: Pull complete
ba41549fd9f6: Pull complete
Digest: sha256:e1eae7579a6a1793d653dd97df9297464600e2644565fa2ed33c351f942facf6
Status: Downloaded newer image for docker/dtr:latest
INFO[0000] Beginning Docker Trusted Registry installation
ucp-password:
INFO[0004] Validating UCP cert
INFO[0004] Connecting to UCP
INFO[0004] health checking ucp
INFO[0004] The UCP cluster contains the following nodes without port conflicts: ip-10-0-1-102, ip-10-0-1-103
INFO[0004] Searching containers in UCP for DTR replicas
INFO[0004] Searching containers in UCP for DTR replicas
INFO[0004] verifying [80 443] ports on ip-10-0-1-102
INFO[0008] Waiting for running dtr-phase2 container to finish
INFO[0008] starting phase 2
INFO[0000] Validating UCP cert
INFO[0000] Connecting to UCP
INFO[0000] health checking ucp
INFO[0000] Verifying your system is compatible with DTR
INFO[0000] Checking if the node is okay to install on
INFO[0000] Using default overlay subnet: 10.1.0.0/24
INFO[0000] Creating network: dtr-ol
INFO[0000] Connecting to network: dtr-ol
INFO[0000] Waiting for phase2 container to be known to the Docker daemon
INFO[0001] Setting up replica volumes...
INFO[0002] Creating initial CA certificates
INFO[0002] Bootstrapping rethink...
INFO[0002] Creating dtr-rethinkdb-729902891973...
INFO[0008] Establishing connection with Rethinkdb
INFO[0009] Waiting for database dtr2 to exist
INFO[0009] Waiting for database dtr2 to exist
INFO[0009] Waiting for database dtr2 to exist
INFO[0010] Generated TLS certificate. dnsNames="[*.com *.*.com example.com *.dtr *.*.dtr]" domains="[*.com *.*.com 172.17.0.1 example.com *.dtr *.*.dtr]" ipAddresses="[172.17.0.1]"
INFO[0011] License config copied from UCP.
INFO[0011] Migrating db...
INFO[0000] Establishing connection with Rethinkdb
INFO[0000] Migrating database schema fromVersion=0 toVersion=10
INFO[0003] Waiting for database notaryserver to exist
INFO[0003] Waiting for database notaryserver to exist
INFO[0003] Waiting for database notaryserver to exist
INFO[0005] Waiting for database notarysigner to exist
INFO[0005] Waiting for database notarysigner to exist
INFO[0006] Waiting for database notarysigner to exist
INFO[0006] Waiting for database jobrunner to exist
INFO[0007] Waiting for database jobrunner to exist
INFO[0007] Waiting for database jobrunner to exist
INFO[0010] Migrated database from version 0 to 10
INFO[0021] Starting all containers...
INFO[0021] Getting container configuration and starting containers...
INFO[0021] Automatically configuring rethinkdb cache size to 2000 mb
INFO[0022] Recreating dtr-rethinkdb-729902891973...
INFO[0028] Creating dtr-registry-729902891973...
INFO[0032] Creating dtr-garant-729902891973...
INFO[0037] Creating dtr-api-729902891973...
INFO[0060] Creating dtr-notary-server-729902891973...
INFO[0064] Recreating dtr-nginx-729902891973...
INFO[0071] Creating dtr-jobrunner-729902891973...
INFO[0077] Creating dtr-notary-signer-729902891973...
INFO[0082] Creating dtr-scanningstore-729902891973...
INFO[0087] Trying to get the kv store connection back after reconfigure
INFO[0087] Establishing connection with Rethinkdb
INFO[0088] Verifying auth settings...
INFO[0088] Successfully registered dtr with UCP
INFO[0088] Installation is complete
INFO[0088] Replica ID is set to: 729902891973
INFO[0088] You can use flag '--existing-replica-id 729902891973' when joining other replicas to your Docker Trusted Registry ClusterNOTE: Don’t forget to change the –ucp-url to Private IP of UCP server
- Once the installation is complete, browse the DTR url
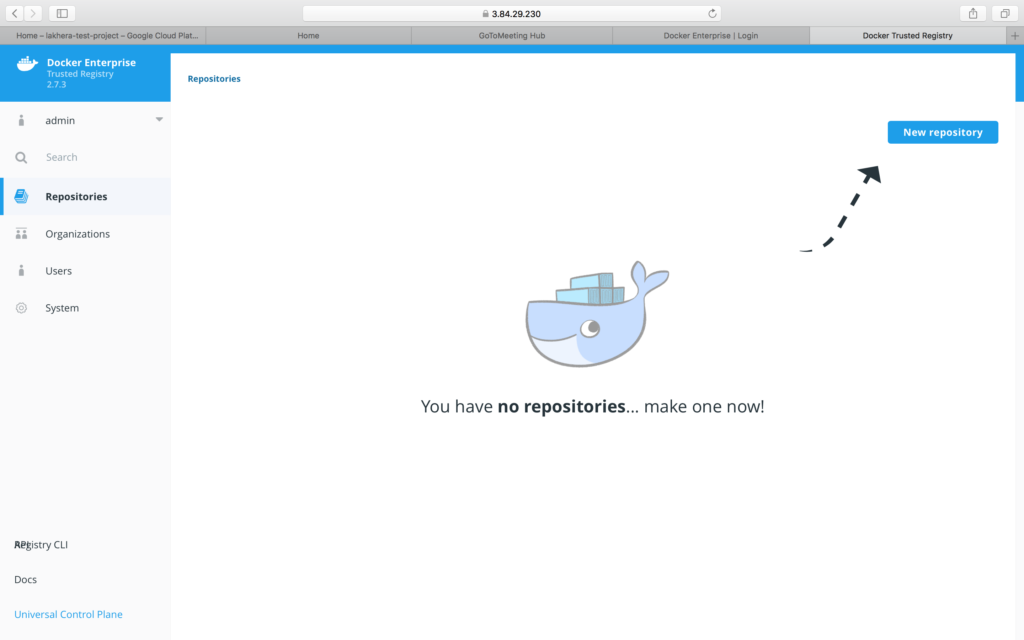
- Note: Once again, a warning about the self-signed certificate’s validity may emerge. This notification can be disregarded
Please follow me with my Journey
- Website:https://100daysofdevops.com/
- Twitter:@100daysofdevops OR @lakhera2015
- Facebook:https://www.facebook.com/groups/795382630808645/
- Medium:https://medium.com/@devopslearning
- GitHub:https://github.com/100daysofdevops/21_Days_of_Docker
This time to make learning more interactive, I am adding
- Slack
- Meetup
Please feel free to join this group.
Slack:
Meetup Group
If you are in the bay area, please join this meetup group https://www.meetup.com/100daysofdevops/

Good day very cool website!! Man .. Beautiful .. Wonderful .. I will bookmark your site and take the feeds I’m satisfied to search out a lot of useful info here in the post, we’d like work out extra techniques in this regard, thanks for sharing. . . . . .
Thanks
Currently it appears like Drupal is the preferred blogging platform out there right now. (from what I’ve read) Is that what you’re using on your blog?
I am using WordPress not sure under the hood which tech it use.
Hello, i think that i saw you visited my weblog thus i came to 搑eturn the favor?I am attempting to find things to improve my site!I suppose its ok to use some of your ideas!!
Sure go ahead