Welcome to Day 2 of 21 Days of AWS using Terraform, Let continue our journey, yesterday I discussed terraform, today let’s build VPC using terraform
What is VPC?
Without going to all the nitty-gritty details of VPC, first, let’s try to understand VPC in the simplest term. Before the cloud era, we use to have datacenters where we deploy all of our infrastructures.

You can think of VPC as your datacentre in a cloud but rather than spending months or weeks to set up that datacenter it’s now just a matter of minutes(API calls). It’s the place where you define your network which closely resembles your own traditional data centers with the benefits of using the scalable infrastructure provided by AWS.
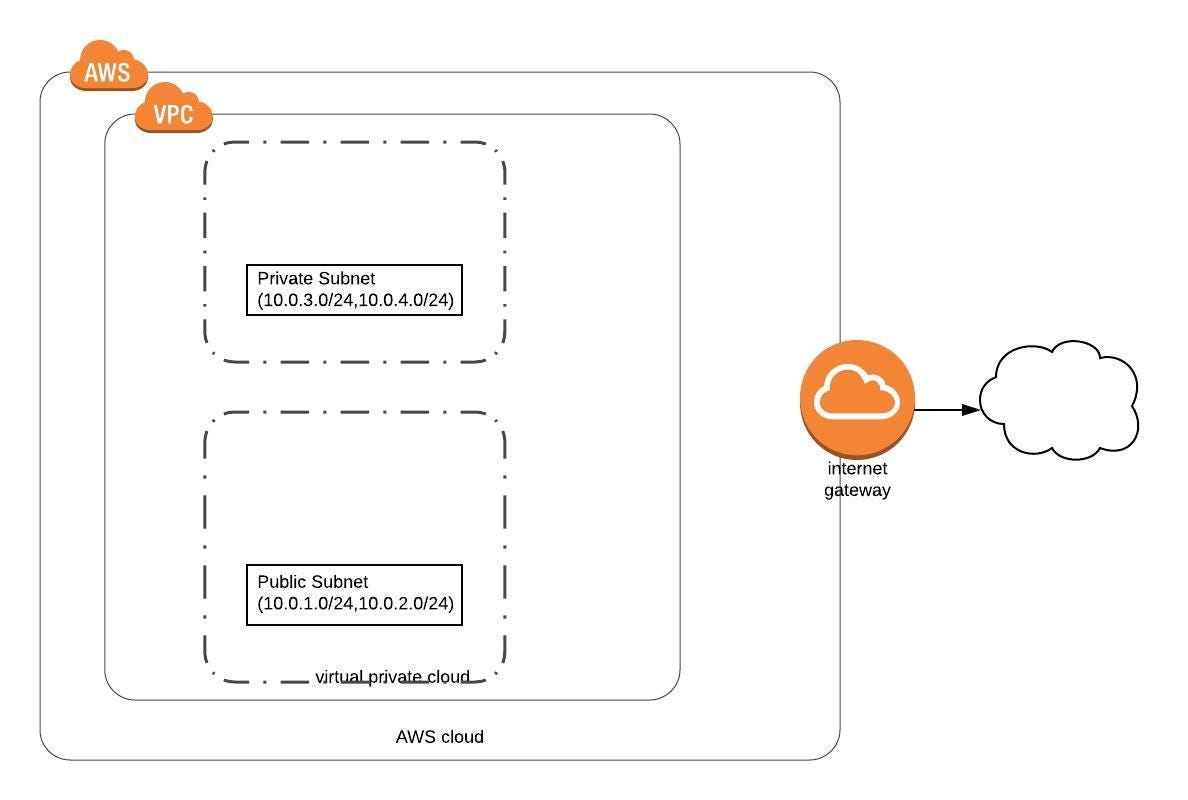
- Today we are going to build the first half of the equation i.e VPC
- Once we create the VPC using AWS Console, these things created for us by-default
* Network Access Control List(NACL) * Security Group * Route Table
- We need to take care of
* Internet Gateways
* Subnets
* Custom Route Table
But the bad news is as we are creating this via terraform we need to create all these things manually but this is just one time task, later on, if we need to build one more VPC we just need to call this module with some minor changes(eg: Changes in CIDR Range, Subnet) true Infrastructure as a Code(IAAC)
- So the first step is to create a data resource, what data resource did is to query/list all the AWS available Availablity zone in a given region and then allow terraform to use those resource.
data "aws_availability_zones" "available" {}https://www.terraform.io/docs/providers/aws/d/availability_zones.html
- Now it’s time to create VPC
resource "aws_vpc" "main" {
cidr_block = "${var.vpc_cidr}"
enable_dns_hostnames = true
enable_dns_support = true
tags = {
Name = "my-new-test-vpc"
}
}cidr_block– The CIDR block for the VPC.enable_dns_support– (Optional) A boolean flag to enable/disable DNS support in the VPC. Defaults true. Amazon provided DNS server(AmazonProvidedDNS) can resolve Amazon provided private DNS hostnames, that we specify in a private hosted zones in Route53.enable_dns_hostnames– (Optional) A boolean flag to enable/disable DNS hostnames in the VPC. Defaults false. This will ensure that instances that are launched into our VPC receive a DNS hostname.
https://www.terraform.io/docs/providers/aws/r/vpc.html
- Next step is to create an Internet Gateway(IGW)
* Internet gateway is a horizontally scaled, redundant and highly avilable VPC component.
* Internet gateway serves one more purpose, it performs NAT for instances that have been assigned public IPv4 addresses.
resource "aws_internet_gateway" "gw" {
vpc_id = "${aws_vpc.main.id}"
tags = {
Name = "my-test-igw"
}
}https://www.terraform.io/docs/providers/aws/r/internet_gateway.html
- Next step is to create Public Route Table
- Route Table: Contains a set of rules, called routes, that are used to determine where network traffic is directed.
resource "aws_route_table" "public_route" {
vpc_id = "${aws_vpc.main.id}"
route {
cidr_block = "0.0.0.0/0"
gateway_id = "${aws_internet_gateway.gw.id}"
}
tags = {
Name = "my-test-public-route"
}
}https://www.terraform.io/docs/providers/aws/r/route_table.html
- Now it’s time to create Private Route Table. If the subnet is not associated with any route by default it will be associated with Private Route table
resource "aws_default_route_table" "private_route" {
default_route_table_id = "${aws_vpc.main.default_route_table_id}"
tags = {
Name = "my-private-route-table"
}
} - Next step is to create Public Subnet
resource "aws_subnet" "public_subnet" {
count = 2
cidr_block = "${var.public_cidrs[count.index]}"
vpc_id = "${aws_vpc.main.id}"
map_public_ip_on_launch = true
availability_zone = "${data.aws_availability_zones.available.names[count.index]}"
tags = {
Name = "my-test-public-subnet.${count.index + 1}"
}
}- Private Subnet
resource "aws_subnet" "private_subnet" {
count = 2
cidr_block = "${var.private_cidrs[count.index]}"
vpc_id = "${aws_vpc.main.id}"
availability_zone = "${data.aws_availability_zones.available.names[count.index]}"
tags = {
Name = "my-test-private-subnet.${count.index + 1}"
}
}https://www.terraform.io/docs/providers/aws/r/subnet.html
- Next step is to create a route table association
# Associate Public Subnet with Public Route Table
resource "aws_route_table_association" "public_subnet_assoc" {
count = 2
route_table_id = "${aws_route_table.public_route.id}"
subnet_id = "${aws_subnet.public_subnet.*.id[count.index]}"
depends_on = ["aws_route_table.public_route", "aws_subnet.public_subnet"]
}
# Associate Private Subnet with Private Route Table
resource "aws_route_table_association" "private_subnet_assoc" {
count = 2
route_table_id = "${aws_default_route_table.private_route.id}"
subnet_id = "${aws_subnet.private_subnet.*.id[count.index]}"
depends_on = ["aws_default_route_table.private_route", "aws_subnet.private_subnet"]
}https://www.terraform.io/docs/providers/aws/r/route_table_association.html
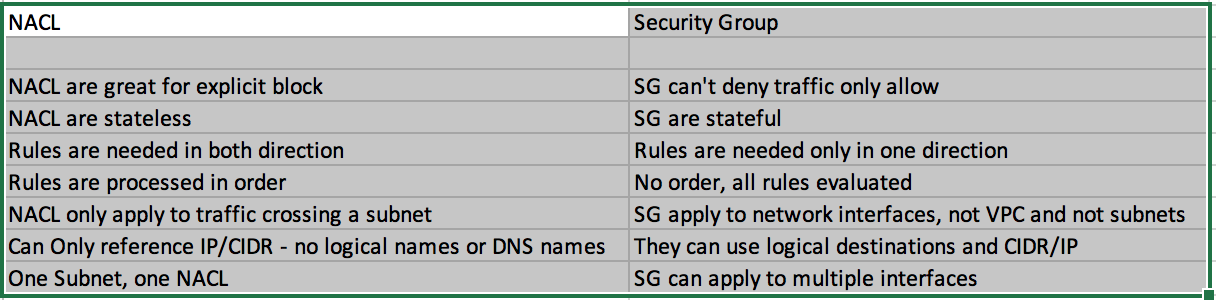
- Network Access Control List(NACL) A network access control list (ACL) is an optional layer of security for your VPC that acts as a firewall for controlling traffic in and out of one or more subnets.
- Security Group acts as a virtual firewall and is used to control the traffic for its associated instances.
- Difference between NACL and Security Group
resource "aws_security_group" "my-test-sg" {
name = "my-test-sg"
vpc_id = "${aws_vpc.my-test-vpc.id}"
}
resource "aws_security_group_rule" "allow-ssh" {
from_port = 22
protocol = "tcp"
security_group_id = "${aws_security_group.my-test-sg.id}"
to_port = 22
type = "ingress"
cidr_blocks = ["0.0.0.0/0"]
}
resource "aws_security_group_rule" "allow-outbound" {
from_port = 0
protocol = "-1"
security_group_id = "${aws_security_group.my-test-sg.id}"
to_port = 0
type = "egress"
cidr_blocks = ["0.0.0.0/0"]
}
https://www.terraform.io/docs/providers/aws/r/security_group.html
- This is how our variables file look like
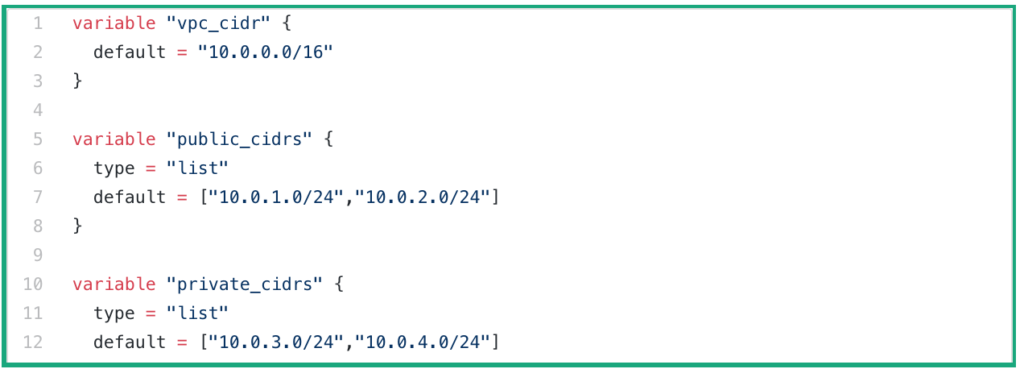
- Now let’s test it
- Initialize a Terraform working directory
$ terraform init
Initializing modules...
- vpc in vpc
Initializing the backend...
Initializing provider plugins...
- Checking for available provider plugins...
- Downloading plugin for provider "aws" (hashicorp/aws) 2.35.0...
The following providers do not have any version constraints in configuration,
so the latest version was installed.
To prevent automatic upgrades to new major versions that may contain breaking
changes, it is recommended to add version = "..." constraints to the
corresponding provider blocks in configuration, with the constraint strings
suggested below.
* provider.aws: version = "~> 2.35"
Terraform has been successfully initialized!
You may now begin working with Terraform. Try running "terraform plan" to see
any changes that are required for your infrastructure. All Terraform commands
should now work.
If you ever set or change modules or backend configuration for Terraform,
rerun this command to reinitialize your working directory. If you forget, other
commands will detect it and remind you to do so if necessary.- Execute terraform plan
- Generate and show an execution plan
$ terraform plan
Refreshing Terraform state in-memory prior to plan...
The refreshed state will be used to calculate this plan, but will not be
persisted to local or remote state storage.
module.vpc.data.aws_availability_zones.available: Refreshing state...
------------------------------------------------------------------------
An execution plan has been generated and is shown below.
Resource actions are indicated with the following symbols:
+ create
Terraform will perform the following actions:
# module.vpc.aws_default_route_table.private_route will be created
+ resource "aws_default_route_table" "private_route" {
+ default_route_table_id = (known after apply)
+ id = (known after apply)
+ owner_id = (known after apply)
+ route = (known after apply)
+ tags = {
+ "Name" = "my-private-route-table"
}
+ vpc_id = (known after apply)
}
# module.vpc.aws_internet_gateway.gw will be created
+ resource "aws_internet_gateway" "gw" {
+ id = (known after apply)
+ owner_id = (known after apply)
+ tags = {
+ "Name" = "my-test-igw"
}
+ vpc_id = (known after apply)
}
# module.vpc.aws_route_table.public_route will be created
+ resource "aws_route_table" "public_route" {
+ id = (known after apply)
+ owner_id = (known after apply)
+ propagating_vgws = (known after apply)
+ route = [
+ {
+ cidr_block = "0.0.0.0/0"
+ egress_only_gateway_id = ""
+ gateway_id = (known after apply)
+ instance_id = ""
+ ipv6_cidr_block = ""
+ nat_gateway_id = ""
+ network_interface_id = ""
+ transit_gateway_id = ""
+ vpc_peering_connection_id = ""
},
]
+ tags = {
+ "Name" = "my-test-public-route"
}
+ vpc_id = (known after apply)
}
# module.vpc.aws_route_table_association.private_subnet_assoc[0] will be created
+ resource "aws_route_table_association" "private_subnet_assoc" {
+ id = (known after apply)
+ route_table_id = (known after apply)
+ subnet_id = (known after apply)
}
# module.vpc.aws_route_table_association.private_subnet_assoc[1] will be created
+ resource "aws_route_table_association" "private_subnet_assoc" {
+ id = (known after apply)
+ route_table_id = (known after apply)
+ subnet_id = (known after apply)
}
# module.vpc.aws_route_table_association.public_subnet_assoc[0] will be created
+ resource "aws_route_table_association" "public_subnet_assoc" {
+ id = (known after apply)
+ route_table_id = (known after apply)
+ subnet_id = (known after apply)
}
# module.vpc.aws_route_table_association.public_subnet_assoc[1] will be created
+ resource "aws_route_table_association" "public_subnet_assoc" {
+ id = (known after apply)
+ route_table_id = (known after apply)
+ subnet_id = (known after apply)
}
# module.vpc.aws_security_group.test_sg will be created
+ resource "aws_security_group" "test_sg" {
+ arn = (known after apply)
+ description = "Managed by Terraform"
+ egress = (known after apply)
+ id = (known after apply)
+ ingress = (known after apply)
+ name = "my-test-sg"
+ owner_id = (known after apply)
+ revoke_rules_on_delete = false
+ vpc_id = (known after apply)
}
# module.vpc.aws_security_group_rule.all_outbound_access will be created
+ resource "aws_security_group_rule" "all_outbound_access" {
+ cidr_blocks = [
+ "0.0.0.0/0",
]
+ from_port = 0
+ id = (known after apply)
+ protocol = "-1"
+ security_group_id = (known after apply)
+ self = false
+ source_security_group_id = (known after apply)
+ to_port = 0
+ type = "egress"
}
# module.vpc.aws_security_group_rule.ssh_inbound_access will be created
+ resource "aws_security_group_rule" "ssh_inbound_access" {
+ cidr_blocks = [
+ "0.0.0.0/0",
]
+ from_port = 22
+ id = (known after apply)
+ protocol = "tcp"
+ security_group_id = (known after apply)
+ self = false
+ source_security_group_id = (known after apply)
+ to_port = 22
+ type = "ingress"
}
# module.vpc.aws_subnet.private_subnet[0] will be created
+ resource "aws_subnet" "private_subnet" {
+ arn = (known after apply)
+ assign_ipv6_address_on_creation = false
+ availability_zone = "us-west-2a"
+ availability_zone_id = (known after apply)
+ cidr_block = "10.0.3.0/24"
+ id = (known after apply)
+ ipv6_cidr_block = (known after apply)
+ ipv6_cidr_block_association_id = (known after apply)
+ map_public_ip_on_launch = false
+ owner_id = (known after apply)
+ tags = {
+ "Name" = "my-test-private-subnet.1"
}
+ vpc_id = (known after apply)
}
# module.vpc.aws_subnet.private_subnet[1] will be created
+ resource "aws_subnet" "private_subnet" {
+ arn = (known after apply)
+ assign_ipv6_address_on_creation = false
+ availability_zone = "us-west-2b"
+ availability_zone_id = (known after apply)
+ cidr_block = "10.0.4.0/24"
+ id = (known after apply)
+ ipv6_cidr_block = (known after apply)
+ ipv6_cidr_block_association_id = (known after apply)
+ map_public_ip_on_launch = false
+ owner_id = (known after apply)
+ tags = {
+ "Name" = "my-test-private-subnet.2"
}
+ vpc_id = (known after apply)
}
# module.vpc.aws_subnet.public_subnet[0] will be created
+ resource "aws_subnet" "public_subnet" {
+ arn = (known after apply)
+ assign_ipv6_address_on_creation = false
+ availability_zone = "us-west-2a"
+ availability_zone_id = (known after apply)
+ cidr_block = "10.0.1.0/24"
+ id = (known after apply)
+ ipv6_cidr_block = (known after apply)
+ ipv6_cidr_block_association_id = (known after apply)
+ map_public_ip_on_launch = true
+ owner_id = (known after apply)
+ tags = {
+ "Name" = "my-test-public-subnet.1"
}
+ vpc_id = (known after apply)
}
# module.vpc.aws_subnet.public_subnet[1] will be created
+ resource "aws_subnet" "public_subnet" {
+ arn = (known after apply)
+ assign_ipv6_address_on_creation = false
+ availability_zone = "us-west-2b"
+ availability_zone_id = (known after apply)
+ cidr_block = "10.0.2.0/24"
+ id = (known after apply)
+ ipv6_cidr_block = (known after apply)
+ ipv6_cidr_block_association_id = (known after apply)
+ map_public_ip_on_launch = true
+ owner_id = (known after apply)
+ tags = {
+ "Name" = "my-test-public-subnet.2"
}
+ vpc_id = (known after apply)
}
# module.vpc.aws_vpc.main will be created
+ resource "aws_vpc" "main" {
+ arn = (known after apply)
+ assign_generated_ipv6_cidr_block = false
+ cidr_block = "10.0.0.0/16"
+ default_network_acl_id = (known after apply)
+ default_route_table_id = (known after apply)
+ default_security_group_id = (known after apply)
+ dhcp_options_id = (known after apply)
+ enable_classiclink = (known after apply)
+ enable_classiclink_dns_support = (known after apply)
+ enable_dns_hostnames = true
+ enable_dns_support = true
+ id = (known after apply)
+ instance_tenancy = "default"
+ ipv6_association_id = (known after apply)
+ ipv6_cidr_block = (known after apply)
+ main_route_table_id = (known after apply)
+ owner_id = (known after apply)
+ tags = {
+ "Name" = "my-new-test-vpc"
}
}
Plan: 15 to add, 0 to change, 0 to destroy.
------------------------------------------------------------------------
Note: You didn't specify an "-out" parameter to save this plan, so Terraform
can't guarantee that exactly these actions will be performed if
"terraform apply" is subsequently run.
- Final step terraform apply
- Builds or changes the infrastructure
$ terraform apply
module.vpc.data.aws_availability_zones.available: Refreshing state...
An execution plan has been generated and is shown below.
Resource actions are indicated with the following symbols:
+ create
Terraform will perform the following actions:
# module.vpc.aws_default_route_table.private_route will be created
+ resource "aws_default_route_table" "private_route" {
+ default_route_table_id = (known after apply)
+ id = (known after apply)
+ owner_id = (known after apply)
+ route = (known after apply)
+ tags = {
+ "Name" = "my-private-route-table"
}
+ vpc_id = (known after apply)
}
# module.vpc.aws_internet_gateway.gw will be created
+ resource "aws_internet_gateway" "gw" {
+ id = (known after apply)
+ owner_id = (known after apply)
+ tags = {
+ "Name" = "my-test-igw"
}
+ vpc_id = (known after apply)
}
# module.vpc.aws_route_table.public_route will be created
+ resource "aws_route_table" "public_route" {
+ id = (known after apply)
+ owner_id = (known after apply)
+ propagating_vgws = (known after apply)
+ route = [
+ {
+ cidr_block = "0.0.0.0/0"
+ egress_only_gateway_id = ""
+ gateway_id = (known after apply)
+ instance_id = ""
+ ipv6_cidr_block = ""
+ nat_gateway_id = ""
+ network_interface_id = ""
+ transit_gateway_id = ""
+ vpc_peering_connection_id = ""
},
]
+ tags = {
+ "Name" = "my-test-public-route"
}
+ vpc_id = (known after apply)
}
# module.vpc.aws_route_table_association.private_subnet_assoc[0] will be created
+ resource "aws_route_table_association" "private_subnet_assoc" {
+ id = (known after apply)
+ route_table_id = (known after apply)
+ subnet_id = (known after apply)
}
# module.vpc.aws_route_table_association.private_subnet_assoc[1] will be created
+ resource "aws_route_table_association" "private_subnet_assoc" {
+ id = (known after apply)
+ route_table_id = (known after apply)
+ subnet_id = (known after apply)
}
# module.vpc.aws_route_table_association.public_subnet_assoc[0] will be created
+ resource "aws_route_table_association" "public_subnet_assoc" {
+ id = (known after apply)
+ route_table_id = (known after apply)
+ subnet_id = (known after apply)
}
# module.vpc.aws_route_table_association.public_subnet_assoc[1] will be created
+ resource "aws_route_table_association" "public_subnet_assoc" {
+ id = (known after apply)
+ route_table_id = (known after apply)
+ subnet_id = (known after apply)
}
# module.vpc.aws_security_group.test_sg will be created
+ resource "aws_security_group" "test_sg" {
+ arn = (known after apply)
+ description = "Managed by Terraform"
+ egress = (known after apply)
+ id = (known after apply)
+ ingress = (known after apply)
+ name = "my-test-sg"
+ owner_id = (known after apply)
+ revoke_rules_on_delete = false
+ vpc_id = (known after apply)
}
# module.vpc.aws_security_group_rule.all_outbound_access will be created
+ resource "aws_security_group_rule" "all_outbound_access" {
+ cidr_blocks = [
+ "0.0.0.0/0",
]
+ from_port = 0
+ id = (known after apply)
+ protocol = "-1"
+ security_group_id = (known after apply)
+ self = false
+ source_security_group_id = (known after apply)
+ to_port = 0
+ type = "egress"
}
# module.vpc.aws_security_group_rule.ssh_inbound_access will be created
+ resource "aws_security_group_rule" "ssh_inbound_access" {
+ cidr_blocks = [
+ "0.0.0.0/0",
]
+ from_port = 22
+ id = (known after apply)
+ protocol = "tcp"
+ security_group_id = (known after apply)
+ self = false
+ source_security_group_id = (known after apply)
+ to_port = 22
+ type = "ingress"
}
# module.vpc.aws_subnet.private_subnet[0] will be created
+ resource "aws_subnet" "private_subnet" {
+ arn = (known after apply)
+ assign_ipv6_address_on_creation = false
+ availability_zone = "us-west-2a"
+ availability_zone_id = (known after apply)
+ cidr_block = "10.0.3.0/24"
+ id = (known after apply)
+ ipv6_cidr_block = (known after apply)
+ ipv6_cidr_block_association_id = (known after apply)
+ map_public_ip_on_launch = false
+ owner_id = (known after apply)
+ tags = {
+ "Name" = "my-test-private-subnet.1"
}
+ vpc_id = (known after apply)
}
# module.vpc.aws_subnet.private_subnet[1] will be created
+ resource "aws_subnet" "private_subnet" {
+ arn = (known after apply)
+ assign_ipv6_address_on_creation = false
+ availability_zone = "us-west-2b"
+ availability_zone_id = (known after apply)
+ cidr_block = "10.0.4.0/24"
+ id = (known after apply)
+ ipv6_cidr_block = (known after apply)
+ ipv6_cidr_block_association_id = (known after apply)
+ map_public_ip_on_launch = false
+ owner_id = (known after apply)
+ tags = {
+ "Name" = "my-test-private-subnet.2"
}
+ vpc_id = (known after apply)
}
# module.vpc.aws_subnet.public_subnet[0] will be created
+ resource "aws_subnet" "public_subnet" {
+ arn = (known after apply)
+ assign_ipv6_address_on_creation = false
+ availability_zone = "us-west-2a"
+ availability_zone_id = (known after apply)
+ cidr_block = "10.0.1.0/24"
+ id = (known after apply)
+ ipv6_cidr_block = (known after apply)
+ ipv6_cidr_block_association_id = (known after apply)
+ map_public_ip_on_launch = true
+ owner_id = (known after apply)
+ tags = {
+ "Name" = "my-test-public-subnet.1"
}
+ vpc_id = (known after apply)
}
# module.vpc.aws_subnet.public_subnet[1] will be created
+ resource "aws_subnet" "public_subnet" {
+ arn = (known after apply)
+ assign_ipv6_address_on_creation = false
+ availability_zone = "us-west-2b"
+ availability_zone_id = (known after apply)
+ cidr_block = "10.0.2.0/24"
+ id = (known after apply)
+ ipv6_cidr_block = (known after apply)
+ ipv6_cidr_block_association_id = (known after apply)
+ map_public_ip_on_launch = true
+ owner_id = (known after apply)
+ tags = {
+ "Name" = "my-test-public-subnet.2"
}
+ vpc_id = (known after apply)
}
# module.vpc.aws_vpc.main will be created
+ resource "aws_vpc" "main" {
+ arn = (known after apply)
+ assign_generated_ipv6_cidr_block = false
+ cidr_block = "10.0.0.0/16"
+ default_network_acl_id = (known after apply)
+ default_route_table_id = (known after apply)
+ default_security_group_id = (known after apply)
+ dhcp_options_id = (known after apply)
+ enable_classiclink = (known after apply)
+ enable_classiclink_dns_support = (known after apply)
+ enable_dns_hostnames = true
+ enable_dns_support = true
+ id = (known after apply)
+ instance_tenancy = "default"
+ ipv6_association_id = (known after apply)
+ ipv6_cidr_block = (known after apply)
+ main_route_table_id = (known after apply)
+ owner_id = (known after apply)
+ tags = {
+ "Name" = "my-new-test-vpc"
}
}
Plan: 15 to add, 0 to change, 0 to destroy.
Do you want to perform these actions?
Terraform will perform the actions described above.
Only 'yes' will be accepted to approve.
Enter a value: yes
module.vpc.aws_vpc.main: Creating...
module.vpc.aws_vpc.main: Creation complete after 5s [id=vpc-0b97129b9e91cac4d]
module.vpc.aws_internet_gateway.gw: Creating...
module.vpc.aws_default_route_table.private_route: Creating...
module.vpc.aws_subnet.private_subnet[0]: Creating...
module.vpc.aws_subnet.private_subnet[1]: Creating...
module.vpc.aws_security_group.test_sg: Creating...
module.vpc.aws_subnet.public_subnet[1]: Creating...
module.vpc.aws_subnet.public_subnet[0]: Creating...
module.vpc.aws_default_route_table.private_route: Creation complete after 2s [id=rtb-034ed4f91b0c6e970]
module.vpc.aws_subnet.private_subnet[0]: Creation complete after 2s [id=subnet-0fb890defa508e1bd]
module.vpc.aws_subnet.private_subnet[1]: Creation complete after 2s [id=subnet-0f210acfcdbb26b1c]
module.vpc.aws_route_table_association.private_subnet_assoc[1]: Creating...
module.vpc.aws_route_table_association.private_subnet_assoc[0]: Creating...
module.vpc.aws_subnet.public_subnet[1]: Creation complete after 2s [id=subnet-0c1da219075f58bbf]
module.vpc.aws_internet_gateway.gw: Creation complete after 2s [id=igw-048be706e974b88cb]
module.vpc.aws_subnet.public_subnet[0]: Creation complete after 2s [id=subnet-0d881fbf8d72978ab]
module.vpc.aws_route_table.public_route: Creating...
module.vpc.aws_route_table_association.private_subnet_assoc[1]: Creation complete after 0s [id=rtbassoc-08c8b58da17951c27]
module.vpc.aws_route_table_association.private_subnet_assoc[0]: Creation complete after 0s [id=rtbassoc-033c1036cbb76fbd3]
module.vpc.aws_security_group.test_sg: Creation complete after 2s [id=sg-05a2779f164a402c7]
module.vpc.aws_security_group_rule.ssh_inbound_access: Creating...
module.vpc.aws_security_group_rule.all_outbound_access: Creating...
module.vpc.aws_security_group_rule.all_outbound_access: Creation complete after 2s [id=sgrule-4135805673]
module.vpc.aws_route_table.public_route: Creation complete after 2s [id=rtb-07f3c3293741dfbaf]
module.vpc.aws_route_table_association.public_subnet_assoc[0]: Creating...
module.vpc.aws_route_table_association.public_subnet_assoc[1]: Creating...
module.vpc.aws_route_table_association.public_subnet_assoc[1]: Creation complete after 0s [id=rtbassoc-06332e5c154dae9d8]
module.vpc.aws_route_table_association.public_subnet_assoc[0]: Creation complete after 0s [id=rtbassoc-02aa98f854d51e7aa]
module.vpc.aws_security_group_rule.ssh_inbound_access: Creation complete after 3s [id=sgrule-2460989827]
Apply complete! Resources: 15 added, 0 changed, 0 destroyed.Terraform Module
- You can think of Terraform Module like any other language module eg: Python, it’s the same terraform file but just that after creating a module out it we can re-use that code OR Instead copy-pasting the code the same code in different places we can turn into reusable modules.
The syntax for the module
module"NAME"{source="SOURCE"
[CONFIG...]}
module "vpc" {
source = "./vpc"
vpc_cidr = "10.0.0.0/16"
public_cidrs = ["10.0.1.0/24", "10.0.2.0/24"]
private_cidrs = ["10.0.3.0/24", "10.0.4.0/24"]
}- variables.tf file look like this
variable "vpc_cidr" {
}
variable "public_cidrs" {
type = "list"
}
variable "private_cidrs" {
type = "list"
}GitHub Link
https://github.com/100daysofdevops/21_days_of_aws_using_terraform
- Looking forward for you guys to join this journey
- Website: https://100daysofdevops.com/
- Twitter: @100daysofdevops OR @lakhera2015
- Facebook: https://www.facebook.com/groups/795382630808645/
- Medium: https://medium.com/@devopslearning
- GitHub: https://github.com/100daysofdevops/100daysofdevops
- Slack: https://join.slack.com/t/100daysofdevops/shared_invite/enQtNzg1MjUzMzQzMzgxLWM4Yjk0ZWJiMjY4ZWE3ODBjZjgyYTllZmUxNzFkNTgxZjQ4NDlmZjkzODAwNDczOTYwOTM2MzlhZDNkM2FkMDA
- YouTube Channel: https://www.youtube.com/user/laprashant/videos?view_as=subscriber
In addition to that, I am going to host 5 meetups whose aim is to build the below architecture.

- Meetup: https://www.meetup.com/100daysofdevops
- Day1(Nov 10): Introduction to Terraform https://www.meetup.com/100daysofdevops/events/266192294/
- Day 2(Nov 16): Building VPC using Terraform
- Day 3(Nov 17): Creating EC2 Instance inside this VPC using Terraform
- Day 4(Nov 23): Adding Application Load Balancer and Auto-Scaling to the EC2 instance created on Day 3
- Day5(Nov 24): Add Backend MySQL Database and CloudWatch Alarm using Terraform

Hi!
Am I missing something?
I’m passing “my_tgw” when I’m prompted for the variables:
”
var.private_cidrs
Enter a value: [“10.0.3.0/24”, “10.0.4.0/24”]
var.public_cidrs
Enter a value: [“10.0.1.0/24”, “10.0.2.0/24″]
var.transit_gateway
Enter a value: my_tgw
var.vpc_cidr
Enter a value: 10.0.0.0/16
”
Error: Error creating route: InvalidTransitGatewayID.Malformed: Invalid id: “my_tgw”
status code: 400, request id: 08729284-2a05-430e-95ad-4732078a48ae
on main.tf line 148, in resource “aws_route” “my-tgw-route”:
148: resource “aws_route” “my-tgw-route” {
Hi Vladimir
This is because of Transit Gateway, Please check Day 14 for the complete info https://100daysofdevops.com/21-days-of-aws-using-terraform-day-14-introduction-to-transit-gateway-using-terraform/
Hi!
Thanks for the reply.
So the code in the /vpc folder will not work on its own, right?
Hi Vladimir
It will, you just need to comment out transit gateway block.